Penetration Testing: Remote Sniffing
|
by Craig Miller
There are times when you may want more detail as to what is happening on your network. Wireshark is an excellent tool to sniff the network, and see what packets are flying by. But it isn't the only tool for network diagnostics.
There is a text-based companion program, tshark which will allow you to sniff the network, but in a terminal (character-based). tshark has the advantage of making it easy to copy/paste packet decodes into other media (such as email).
An of course, there is tcpdump which has been around for decades, but is still a very useful tool, which runs just about everywhere.
Wireshark
We have covered Wireshark in 2019, and it is still a good tutorial. Packet filtering can be performed at capture time (using tcpdump syntax) or once packets have been captures, aka display filtering.
Remote Sniffing
Wireshark will happily sniff the network you are on, but what if you need to look at a network your laptop is not directly connected. How would you do that?
Option A: Install tcpdump or tshark on a remote machine attached to the remote network, and then sniff interactively, or write pcap files, and scp the pcap files back to your laptop.
Option B: Use the remote sniffing capability built into Wireshark. This is the option we will be demonstrating into the lab today.
Remote Sniffing requirements
In order to perform remote sniffing with Wireshark, one needs the following:
- Wireshark installed on your laptop
- A remote device, with
tcpdumpinstalled - Access to the remote device via
sshand root login- OpenWrt routers are perfect for this
Implementing Option B: Remote Sniffing
OpenWrt routers are perfect for remote sniffing, since they meet the requirements (above) and routers tend to funnel traffic, which means you will see more in the packet capture.
- Add your wireshark user to the group
wireshark, you may need to re-login, or start a new shell - Start Wireshark interactive UI
- Click on the Gear Icon to the left of "SSH remote capture" interface, and enter host and authentication info
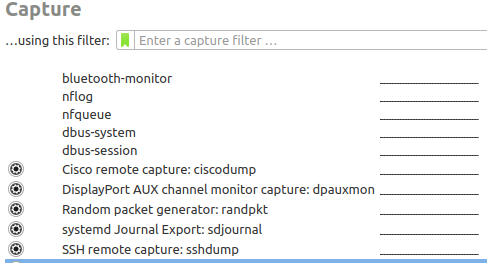
- Fill remote host address + SSH credentials of the target machine. This is a good place to use
ssh keys, in the lab we will use simple passwords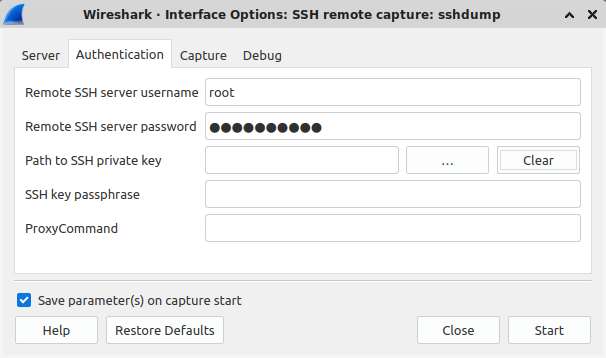
- Fill out the correct interface to sniff, and ensure there is a packet filter to ignore ssh (typically
not port 22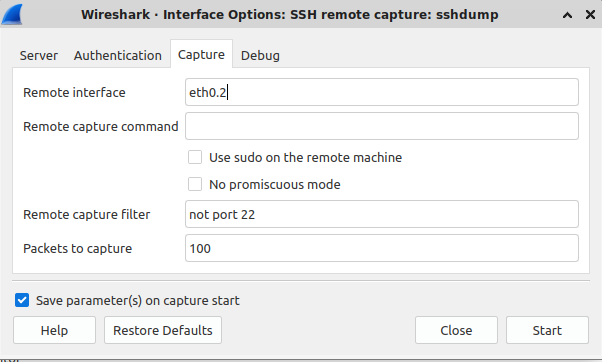
- Click on start to capturing packets
If it is all working correctly, you should see packets showing up in Wireshark.
When things go wrong
As you can see above, there are a few steps to follow to use this technique. The most common error I have run into is this one:
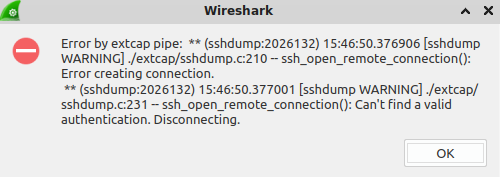
The important part is right at the end: "Can't find a valid authentication. Disconnecting." This usually means that wireshark has forgotten the password, and it needs to be re-entered.
1. Hands On - Basic Remote Sniffing
Start wireshark, using SSH Remote capture, capture at least 10 packets Use the following information to:
- host: waimea
- Remote ssh server port: 22
- password: (ask me)
- remote interface: br-lan
- remote capture filter: 'not port 22'
Attempt/Answer the following:
- Did you get an error when starting the capture?
- Does your capture include SSH packets?
- Why would you limit the number of packets to capture?
- How can you limit the capture to just one protocol?
- Extra Credit: What is the IP address of the host initiating a ping?
Caveats regarding remote sniffing
Although OpenWrt routers are great network probes, the interfaces differ depending on the HW manufacturer of the router. There will always be a br-lan. However if you want to sniff the upstream interface, you will need to know the device name (e.g. eth0 or eth0.2, etc). The only reliable way to determine this is to log into the router and use the ip addr command to see the other interface with IP addresses (other than br-lan)
The downside of the technique is that one needs root access on the remote host. Only root can do a promiscuous sniff of an interface. But setting up ssh keys will make this remote root login more secure. OpenWrt support ssh keys via the web interface (LuCI).
Conclusion
This is just another tool in your examination of Penetration Testing. Being able to capture packets on a remote network will help you debug network issues that much quicker. Proactively creating a network with probes, ready to remote sniff, will make fixing network issues even faster.
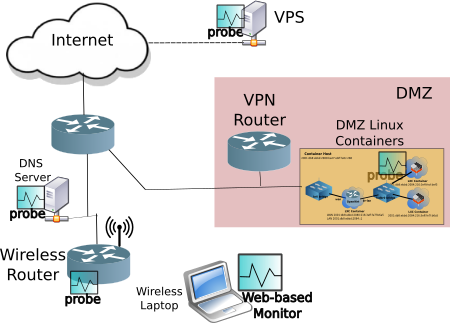
Notes:
- OpenWrt discussion about remote sniffing (forum.openwrt.org)
- Network with probes from Camosun Capstone project proposal
- Adding a ssh key is not all that hard:
- Create a key
ssh-keygen -t rsa -f wireshark -C Wireshark - Place the
wireshark.pubpublic key on the OpenWrt router (via the web management page) - In
wiresharkin the "ssh remote capture" dialog click on the "Path to SSH private key" and find thewiresharkprivate key file. - Continue the "SSH remote capture" parameters (interface, etc) and click Start
- Create a key
24 April 2024