Tools: Wireshark: Network Protocol Analyzer
the Open Source Packet Sniffer |
by Craig Miller
Anytime we surf the internet, there is a flury of packets crossing the expanse from here to a server in some remote location. As long as it all works, we don't think about the nuts and bolts of how it all works.
But when it doesn't work, it is time to dig down into the packet stream and figure out what has gone wrong. Enter the packet sniffer.
History
Back in the 1990s there were expensive lunch-box-size computers specifically made to sniff computer networks which cost thousands of dollars.
In 1988 tcpdump was written under the BSD license. tcpdump is a CLI-based application which has extensive capture filters to help the user zero in on the packets of interest.
Almost ten years later, in late 1997, Gerald Combs, started ethereal a graphical packet sniffer application.
In 2006, Combs changed the name of the packet sniffer application to wireshark, as Ethereal trademark was held by a private company.
Packet Header Structure
Before diving into Wireshark, it is important to know how network packets are structured. Typically there is a header with some fixed information, possibly a version field, and then most importantly, a next header field. It is the next header field which tells the protocol decoder how to interpret the next chunk of bits.
For example, the IP headers looks like:
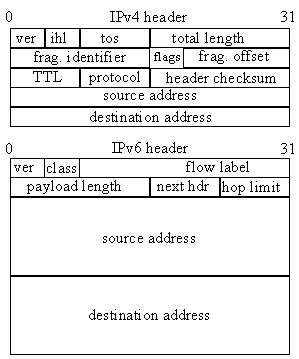
In the IPv4 header there is a protocol field which describes the next header. The same field is called next hdr in the IPv6 header.
The IANA (Internet Assigned Numbers Authority) is the authority of protocol numbers. BTW, IANA also retains the IP Version numbers as well, where you will see that versions 5, 7, 8, and 9 have been moved to historic (deprecated) status.
Wireshark Intro
The wireshark application window is divided into 3 major parts (see screen shot).
- Packet List
- Packet Details
- Packet Bytes
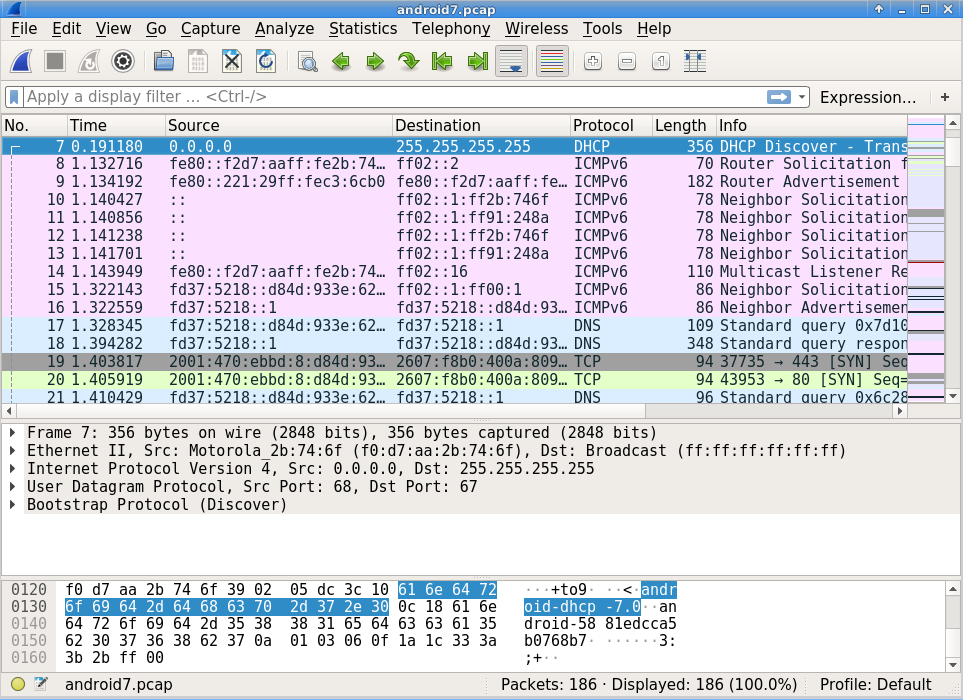
There are many tutorials online for wireshark, including one from wireshark.org
1. Hands On - Wireshark First Look
Start wireshark and capture about 10 seconds of network activity.
Attempt/Answer the following:
- How did you start Wireshark?
- What interface did you sniff?
- What type(s) of packets did you capture?
Hands On Discussion
Before there was IPv4, there were many protocols using Ethernet Layer 2 Transport. IANA has an extensive list of ethertypes
Packet Filtering
Looking at a busy network can be like drinking from a firehose. There needs to be a way of sifting the wheat from the chaff or if you prefer, zooming in on the packets of interest.
There are two packet filtering mechanisms in wireshark.
- Capture filter
- Display filter
The syntax of these filters are not the same. Because wireshark was created after tcpdump the author used the tcpdump capture filter syntax in wireshark. Capture filters prevent your machine, which keeps all the packets in memory, from running out of resources.
Display filters are excellent for tracking a set of packets already captured (such as Follow TCP Stream).
2. Hands On - Wireshark packet filtering
Use Display Filters on the 10 second capture you did in the first lab.
Attempt/Answer the following:
- How many
ippackets are captured? - How many
ipv6packets have been captured? - What is the
ethertypenumber for IPv4?
Packet Filter (part 2)
Capture filters syntax is the same as tcpdump. They allow you to run a capture for a long time while monitoring only certain packets on the network. Some examples are:
iponly capture IPv4 packetsicmpcapture ICMP (ping) packetsip6only capture IPv6 packetsicmp6capture ICMPv6 packets (Neighbour Discovery, Router Adv, etc)port 80capture traffic on port 80 (TCP or UDP)
The tcpdump filters cheat sheet is very handy for creating capture filters in Wireshark.
Using capture filters in Wireshark
Clicking on the gear icon (capture options) will open a dialog for selecting an interface and capture filter at the bottom. If wireshark recognizes the capture filter, it will display the field in green (similar to the visual indication of display filters).
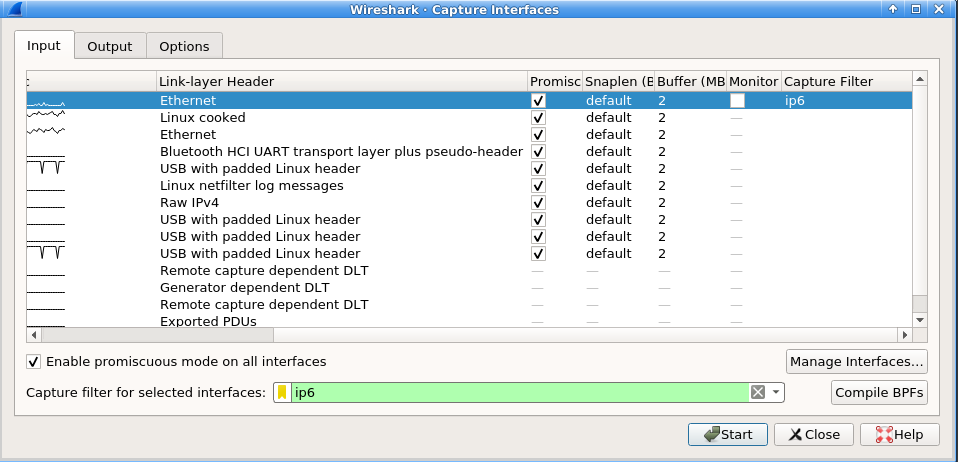
3. Hands On - Wireshark capture filtering
Use Capture Filters to:
Attempt/Answer the following:
- Capture just ping packets. What filter did you use?
- Do another capture for just IPv6 ping packets. What filter did you use?
- Do another capture for just Router Advertisements. What prefix(s) is/are advertised?
Hands On Discussion
It is possible to use AND and OR in your capture filters. Additionally, it is possible to address specific bytes or even bits in a header. For example, since RAs are ICMP type 134, to create a capture filter, one would use:
icmp6 and ip6[40]=134
TCP Follow Stream (with help from netcat)
Wireshark not only displays packets with extensive packet decode, but can also so some analysis such as following a TCP stream. Using Netcat, a CLI utility to open a socket to a remote host, and send text, we create a simple (sniffable) TCP stream.
By selecting a TCP packet and then going to the Menu->Analyze->Follow->TCP Stream, wireshark will display the payload of that TCP stream.
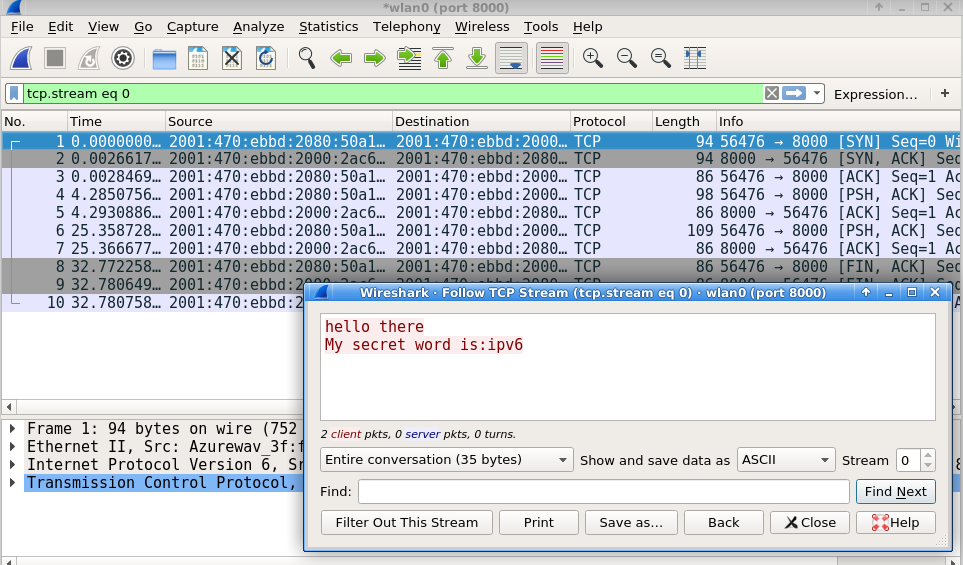
4. Demo - Wireshark Following a TCP Stream
Use Capture Filter only insecure FTP traffic, on the router. Ask class members to attempt login to the insecure FTP server. Pull up capture file in Wireshark.
Discuss the following:
- Capture just port 21. What filter should be used?
- Do you see the TCP 3-way handshake? What are the 3 packets representing the 3-way handshake?
- What text does TCP Follow display?
Using Wireshark with tcpdump & sshfs (poor man's cloudshark)
There used to be a really useful program made available on OpenWrt for free, called Cloudshark. It is a Cloud-based implementation of Wireshark. Alas, Cloudshark is no longer free, still a nice utility if you need such a thing.
However using tcpdump, sshfs and Wireshark we can simulate Cloudshark's capabilities. In order to do this, we'll need to have tcpdump, sshd and sftpd installed on the remote device/computer. And of course, we'll need Wireshark installed on our local computer (e.g. our laptop).
-
Set up
sshfsto mount a temporary directory from the remote device (e.g. /tmp). And thensshto the remote device. -
Using
tcpdumpcapture the packets of interest and write the pcap file to the temporary directory. -
Use the local copy of Wireshark to open the pcap file (over the
sshfsmount). -
Enjoy the power of Wireshark analysis on a device that doesn't support Wireshark.
Cloud/Wireshark Demo
Summary
Wireshark is a powerful open-source network sniffing tool which allows one to see what is really happening on the network. It allows you to discover what that app or IoT device is really doing. Is it phoning home every time you start it? Are the communications encrypted? If not, use TCP Follow Stream to see what is being transmitted.
Wireshark allows you to open up your network and peek inside.
*Wireshark logo (creative commons)
*TCPDump cheat sheet (from Marios Iliofotou)
last updated: 23 August 2019