The details behind Wifi: 802.11a,b,g,n,ac,ax, & ay
|
by Craig Miller
Wireless technology has become ubiquitous with our cellphones, laptops, PDAs, IoT devices, mice and keyboards. Bicycle cyclometers even use wireless to get speed info from the sensor.
But it wasn't always this way. There was a time when wires were king. A computer was some clunky thing in the corner of a room with a heavy CRT (Cathode Ray Tube) for a display, hooked to a dial-up modem.
So how did we get here, the glorious world of no wires?
History
In the beginning there was Marconi transmitting Morse code across the Atlantic Ocean in 1901. But perhaps we don't have to go that far back.
The IEEE (Institute for Electrical and Electronics Engineers) standardized 802.11b, what we know as Wifi, in 1999. The b sub-standard uses the FCC designated ISM 2.4 Ghz band. The very same band which is used by the Microwave Oven in your kitchen.
Through the last 20 years, the IEEE has been improving and expanding the 802.11 protocol adding the substandards: g,n, and ac, each faster than the previous one.
Wifi Spectrum
The 2.4 Ghz band is divided up into eleven 5 Mhz channels (in North America). But each of the 20 Mhz-wide-RF-signals overlap the adjacent two channels on either side. Only channels 1, 6, and 11 don't overlap.
.svg.png)
Fortunately the 5 Ghz band is less constrained and channels were thought of with 20 Mhz use in mind.
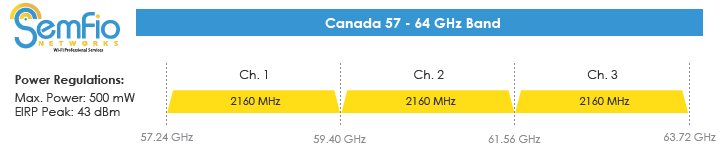
The next Wifi Band: 60 Ghz
And with 802.11ad (and 802.11ay) the 60 Ghz band will be available. There will be three (3) 2.16 Ghz wide channels available in North America. Because the 60 Ghz band is also the Oxygen absorption band, the range will pretty much be limited to rooms (it doesn't penetrate paint very well).
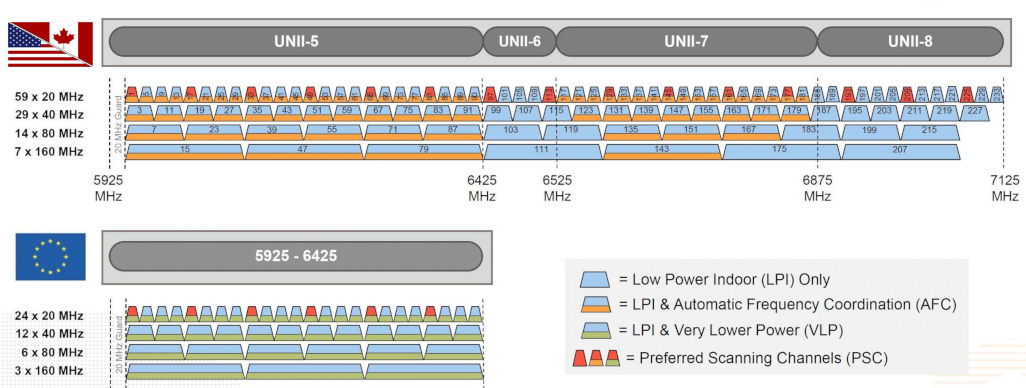
And in 2020, the 6 Ghz band, aka Wifi6E
From the Wifi Allance.
"6 GHz addresses Wi-Fi spectrum shortage by providing contiguous spectrum blocks to accommodate 14 additional 80 MHz channels and 7 additional 160 MHz channels"
In the US, the FCC will vote in April, 2020 to open 6 Ghz as unlicensed spectrum.
APs, Managed, and Ad-Hoc
The vast majority of 802.11 wireless you will encounter will be Managed APs (Access Points). There was a time when it was thought that Ad-Hoc would be quit useful, but it is rarely found these days.
A Managed AP, means that the Access Point itself is controlling the speakers (the wireless clients), giving time for each to transmit data. While this method works well, it introduces a fair bit of latency in the communications while each client waits to be called up by the AP.
As part of the Management, the AP also sends a beacon frame with the SSID (and BSSID), allowing potential clients to join the AP.
Beacons
Beacon frame describe quite a bit of information about the AP, including data rates, Cyphers supported, channel width and many other capabilities.
IEEE 802.11 wireless LAN
Fixed parameters (12 bytes)
Timestamp: 0x0000041c2990812d
Beacon Interval: 0.102400 [Seconds]
Capabilities Information: 0x0431
.... .... .... ...1 = ESS capabilities: Transmitter is an AP
.... .... .... ..0. = IBSS status: Transmitter belongs to a BSS
.... ..0. .... 00.. = CFP participation capabilities: No point coordinator at AP (0x00)
.... .... ...1 .... = Privacy: AP/STA can support WEP
.... .... ..1. .... = Short Preamble: Allowed
.... .... .0.. .... = PBCC: Not Allowed
.... .... 0... .... = Channel Agility: Not in use
.... ...0 .... .... = Spectrum Management: Not Implemented
.... .1.. .... .... = Short Slot Time: In use
.... 0... .... .... = Automatic Power Save Delivery: Not Implemented
...0 .... .... .... = Radio Measurement: Not Implemented
..0. .... .... .... = DSSS-OFDM: Not Allowed
.0.. .... .... .... = Delayed Block Ack: Not Implemented
0... .... .... .... = Immediate Block Ack: Not Implemented
Tagged parameters (148 bytes)
Tag: SSID parameter set: Waipahu
Tag Number: SSID parameter set (0)
Tag length: 7
SSID: Waipahu
Tag: Supported Rates 1(B), 2(B), 5.5(B), 11(B), 22, 6, 9, 12, [Mbit/sec]
Tag: Extended Supported Rates 18, 24, 36, 48, 54, [Mbit/sec]
Tag: RSN Information
Tag Number: RSN Information (48)
Tag length: 20
RSN Version: 1
Group Cipher Suite: 00:0f:ac (Ieee 802.11) AES (CCM)
Group Cipher Suite OUI: 00:0f:ac (Ieee 802.11)
Group Cipher Suite type: AES (CCM) (4)
Pairwise Cipher Suite Count: 1
Pairwise Cipher Suite List 00:0f:ac (Ieee 802.11) AES (CCM)
Pairwise Cipher Suite: 00:0f:ac (Ieee 802.11) AES (CCM)
Pairwise Cipher Suite OUI: 00:0f:ac (Ieee 802.11)
Pairwise Cipher Suite type: AES (CCM) (4)
Auth Key Management (AKM) Suite Count: 1
Auth Key Management (AKM) List 00:0f:ac (Ieee 802.11) PSK
Auth Key Management (AKM) Suite: 00:0f:ac (Ieee 802.11) PSK
Auth Key Management (AKM) OUI: 00:0f:ac (Ieee 802.11)
Auth Key Management (AKM) type: PSK (2)
RSN Capabilities: 0x000c
.... .... .... ...0 = RSN Pre-Auth capabilities: Transmitter does not support pre-authentication
.... .... .... ..0. = RSN No Pairwise capabilities: Transmitter can support WEP default key 0 simultaneously with Pairwise key
.... .... .... 11.. = RSN PTKSA Replay Counter capabilities: 16 replay counters per PTKSA/GTKSA/STAKeySA (0x3)
.... .... ..00 .... = RSN GTKSA Replay Counter capabilities: 1 replay counter per PTKSA/GTKSA/STAKeySA (0x0)
.... .... .0.. .... = Management Frame Protection Required: False
.... .... 0... .... = Management Frame Protection Capable: False
.... ...0 .... .... = Joint Multi-band RSNA: False
.... ..0. .... .... = PeerKey Enabled: False
1. Hands On - Look at a Beacon
Download the Beacon Frame PCAP and examine in Wireshark
Discuss the following: * What is the SSID? * What is the BSSID? * What channel is the Beacon transmitted?
Sniffing 802.11 frames
Capturing 802.11 frames is difficult for a couple of reasons:
- The wireless driver creates a pseudo-ethernet interface, and hides much if not all of the wireless details
- Most wireless interface cards are designed for the consumer market (read: to be used on a laptop or cell phone) and don't support monitor mode.
Determining if your Wireless supports Monitor Mode
The iw list command will display lots of information about your wireless interface(s), including the frequencies supported, and the supported interface modes:
root@Nanakuli:~# iw list
Wiphy phy0
max # scan SSIDs: 4
...
Supported interface modes:
* IBSS
* managed
* AP
* AP/VLAN
* monitor
* mesh point
* P2P-client
* P2P-GO
...
If monitor mode is not supported on your wireless interface, you will not be able to sniff 802.11 frames.
Kali Linux, a distro designed for network test has a list of supported USB Dongles that support monitor mode.
Using Monitor Mode
When capturing 802.11 frames, one must put the interface in monitor mode. When this happens the interface is disassociated from the AP it may be connected to and put into a special listening mode. Once the interface is in monitor mode it can hear both the AP and clients of the AP. If there are multiple APs on a specific channel, it will hear those as well.
However because in the modern world, APs use some form of encryption (WEP, WPA, etc), and the interface is no longer associated with the AP, it no longer has the encryption key, and therefore the captured packets will be the 802.11 header and opaque DATA.
Wireshark can decode an 802.11 capture on a non-encrypted AP.
Another method to find out if your wireless card supports monitor mode is to use the following command with tcpdump
tcpdump -i wlan0 --monitor-mode
What is one to do if your wireless interface does not support monitor mode?
OpenWrt can sniff 802.11
Routers are designed to use 802.11 Wireless, and not only just be clients of other wireless networks, but also to be APs. OpenWrt can put its wireless interface into monitor mode (via the LuCI web interface), and one can use tcpdump to capture 802.11 frames.
root@openwrt:~# tcpdump -i wlan0 -vvv
tcpdump: listening on wlan0, link-type IEEE802_11_RADIO (802.11 plus radiotap header), capture size 262144 bytes
01:14:40.352794 10973171us tsft 1.0 Mb/s 2452 MHz 11b -24dBm signal -30dBm signal antenna 0 -25dBm signal antenna 1 Beacon (Tolbiac2.4) [1.0* 2.0* 5.5* 11.0* 6.0 9.0 12.0 18.0 Mbit] ESS CH: 9, PRIVACY
01:14:40.355231 10975762us tsft 1.0 Mb/s 2452 MHz 11b -61dBm signal -70dBm signal antenna 0 -62dBm signal antenna 1 Beacon (Waipahu) [1.0* 2.0* 5.5* 11.0* 22.0 6.0 9.0 12.0 Mbit] ESS CH: 3, PRIVACY
01:14:40.455184 11075572us tsft 1.0 Mb/s 2452 MHz 11b -25dBm signal -30dBm signal antenna 0 -26dBm signal antenna 1 Beacon (Tolbiac2.4) [1.0* 2.0* 5.5* 11.0* 6.0 9.0 12.0 18.0 Mbit] ESS CH: 9, PRIVACY
01:14:40.457615 11078162us tsft 1.0 Mb/s 2452 MHz 11b -62dBm signal -76dBm signal antenna 0 -62dBm sign
...
^C
20 packets captured
20 packets received by filter
0 packets dropped by kernel
Note that --monitor-mode wasn't used, as the interface was placed into monitor mode via the OpenWrt LuCI web interface
The smallest commercially available OpenWrt router, GL.iNET USB150 micro-router, appears to look like a Wifi USB Dongle, but has full routing capability including monitor mode as well.

Another way to see Beacon Frame information
Beacon frames are designed to convey information about the AP to all comers. Therefore there are other methods that examining the 802.11 frames directly to see the information.
WICD
WICD, or Wireless Connection Manager daemon, can also be used to scan available wireless netwworks with your laptop.
Not unlike many applications on linux, there are two parts, a daemon or server which runs in the background, and client apps which access the data from the daemon, and display it for the user.
Because, the daemon is accessing the wireless interface, it requires root privilages. Start it by:
sudo wicd
There is a GUI client app, wicd-gtk with has lots of GUI friendliness. Start it with:
wicd-gtk
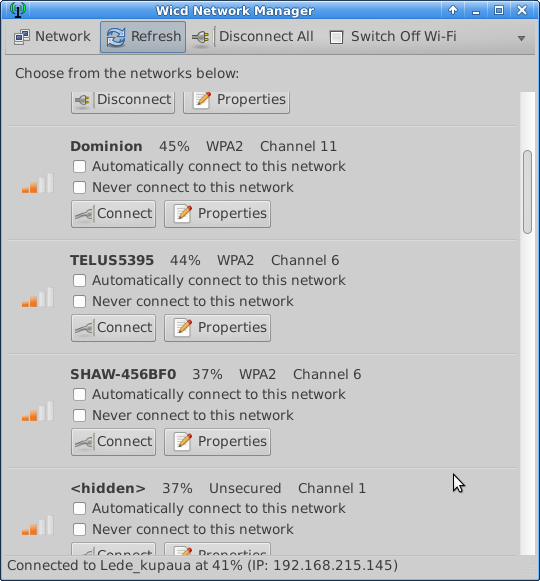
Reading Wireless Beacon Info with WICD
But I find the curses client provides more information on a single screen. Start the curses client with:
wicd-curses
For wireless beacon info there are only a couple of commands you need to use. * R to refresh the list * Q to quit the app
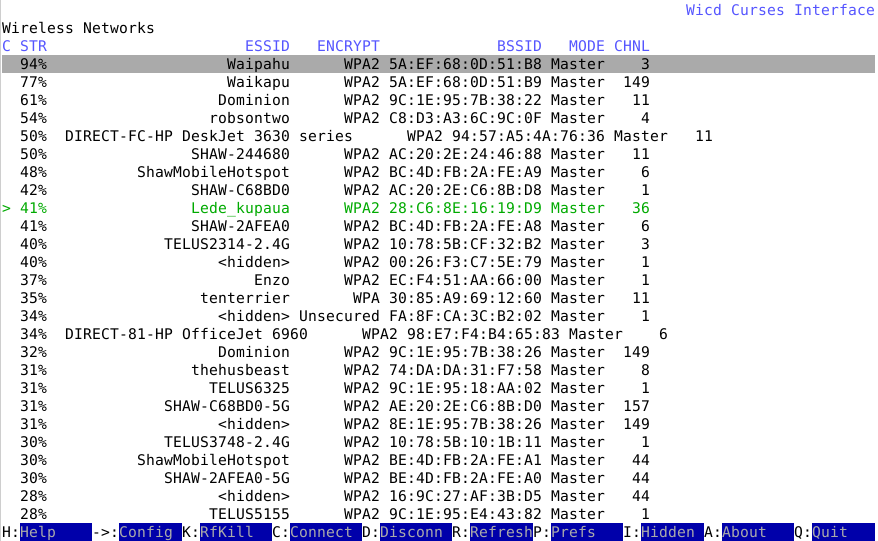
2. Hands On - Looking at Beacon Info
Install and run wicd and wicd-curses
Discuss the following: * What is the strongest SSID? * What is the manufacturer of the strongest SSID? * How many 5 Ghz APs are available?
OSI Layered Model of Networking
The Open Systems Interconnection model (OSI model) is the reference by which all modern networks use. It comprises 7 layers from Physical to Application. By keeping functions limited to a single layer, it ensures interopability with the other layers of the model.
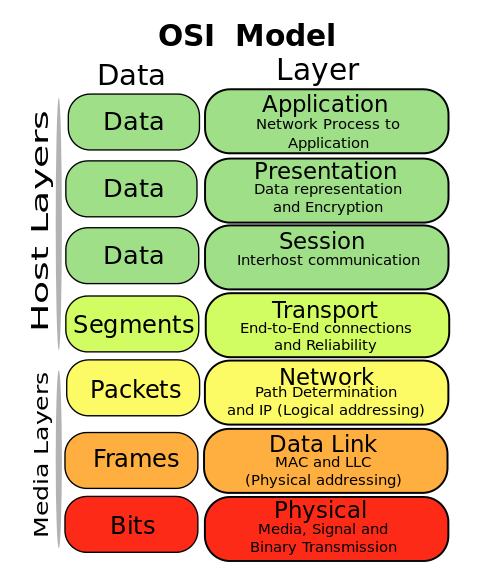
Of course, when the OSI model was created in the late 1970s, there was no 802.11 wireless. And therefore, when the IEEE created 802.11, the Physical layer is really the radios which transmit and receive the signals. 802.11 frames are part of layer 2 (the Data Link), and the pseudo-ethernet that the driver presents is also layer 2.
Connecting to Wireless
There are specific terms when connecting networks via Layer 2 (Bridging) and Layer 3 (Routing). Because 802.11 wireless only presents a pseudo-ethernet, it can't be bridged but must be routed. The exception to this is when the device is the AP. Since the AP is the master, it controls the entire wireless network and is bridged (think: home router LAN ports are bridged to the wireless by default).
Wifi Bridging can be done with WDS (Wireless Distribution System). Although WDS is rarely supported on end-station wireless interfaces, OpenWrt does support WDS on most of the routers, allowing one to create a large wireless network, but utilizing a single subnet (or IPv6 prefix).
Most end-stations (read: laptops, cell phones, etc) use routing to access the wireless interface. The Interface will have an IP (4 and/or 6) address (Network Layer).
Wireless Mesh
The 802.11s standard defines a non-client-server mode allowing routing nodes to be connected in a mesh topology. OpenWrt supports 802.11s but may require a loop-prevention routing protocol like Babel or BATMAN. Wireless Mesh is for routers.
End nodes, like laptops, phones, etc. will still connect to a Mesh node (aka router) using the common AP-Wireless-Client mode.
Other Wireless Technologies
There are other wireless technologies which also use the ISM spectrum. With a spectrum analyzer it is possible to see other uses. Some of the more common ones are:
- Bluetooth
- Cordless Phones
- Microwave Ovens (2.4 Ghz only)
- Wireless mice and keyboards
Other Wireless Technologies * 6LoWPAN IEEE 802.15.4 & Mesh Routing * Smart Grid & Smart Meters * LoRa on 433 & 915 Mhz
Everything Wireless
Peeling back the onion of wireless protocols, such as 802.11, helps reveal some of the magic which we use everyday. The Internet has given us world-wide connectivity, but wireless has given us true connected freedom.
30 March 2020
Updated 15 Feb 2025 with 6Ghz spectrum chart