PPPoX -A Technology Primer
Agenda
- Introduction
- History of PPP
- Point to Point Protocol
- Phases of PPP
- Types of Authentication
- PAP
- CHAP
- New Use of PPP -- Broadband
- Accounting
- Types of PPP in Broadband
- PPPoE
- PPPoEoA
- PPPoA
- Testing PPPoX
- Understanding
how the Cisco Terminates PPPoE
- References
Introduction
- PPP is more than just a dial up access technology
- PPP has been recognized as a thin transport technology (adding only 2 bytes)
- PPP is utilized for Packet over SONet (PoS)
- PPPoX is being deployed as a Broadband Access Technology
History
- Sucessor to SLIP (Serial Line Internet Protocol) - RFC 1055
- Written by Rick Adams of UUNET on BSD in1984
- Internet Standard in 1994 - RFC 1661
- Initially written in Dec 1993 - RFC 1548
Point to Point Protocol
The Point-to-Point Protocol (PPP) provides a standard method for transporting multi-protocol datagrams over point-to-point links. PPP is comprised of three main components:
- A method for encapsulating multi-protocol datagrams.
- A Link Control Protocol (LCP) for establishing, configuring, and testing the data-link connection.
- A family of Network Control Protocols (NCPs) for establishing and configuring different network-layer protocols.
- Low Speed environments where encapsulation can be shortened to only 2 or 4 bytes
- High Speed environments -- the default encapsulation uses only simple fields, only one of which needs to be examined for demultiplexing
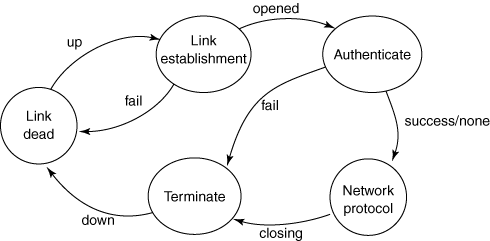
Phases of PPP
- Dead
- Establish
- Autenticate
- Network
- Terminate
Types of Authentication
Password Authentication Protocol (PAP )PAP works basically the same way as the normal login procedure. The client authenticates itself by sending a user name and an (optionally encrypted) password to the server, which the server compares to its secrets database. This technique is vulnerable to eavesdroppers who may try to obtain the password by listening in on the serial line, and to repeated trial and error attacks.
- Two Way Handshake
- Boston sends Password in the clear
- Atlanta Accepts or Rejects the password
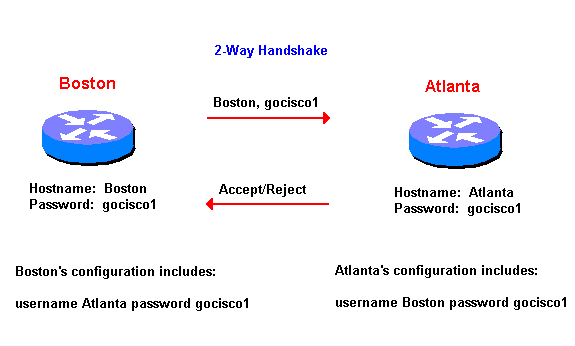
Fig. 2 PAP
Challenge Handshake Authentication Protocol (CHAP)
The authenticator (i.e. the server) sends a randomly generated ``challenge'' string to the client, along with its hostname. The client uses the hostname to look up the appropriate secret, combines it with the challenge, and encrypts the string using a one-way hashing function. The result is returned to the server along with the client's hostname. The server now performs the same computation, and acknowledges the client if it arrives at the same result.
- 3 Way Handshake
- Atlanta sends Challenge
- Boston sends response
- Atlanta Accepts or Rejects encrypted response
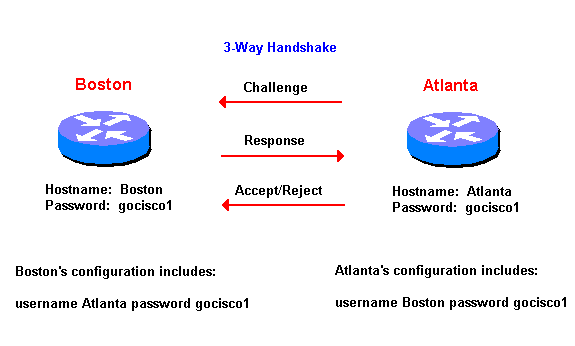
Fig.3 CHAP
New Use of PPP
- Broadband Access
- DSL
- Cable? Why not?
- Accounting
- Re-use of an old use - Only accept authenticated users
- Permits Service to be metered
Types of PPP in Broadband
- PPPoA
- Defined by RFC 2364
- Encapsuation of a single PPP session per VC (VPI/VCI)
- PPPoEoA
- Not defined currently by a RFC
- Encapsulation of multiple PPP sessions per VC (VPI/VCI)
- PPPoE
- Defined by RFC 2516
- Encapsulation of PPP over Ethernet
PPPoA
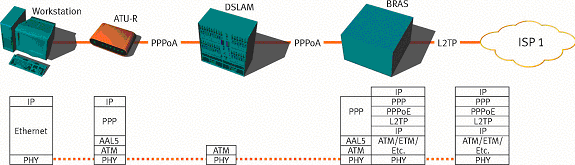
Fig. 4 PPPoA
PPPoEoA
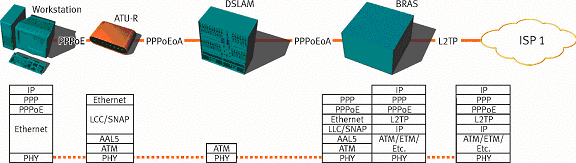
Fig. 5 PPPoEoA
Testing PPPoX
Service providers are all anxious to sell broadband Internet services. However, like all service provider business models, broadband services will only be financially successful if they can be deployed and accepted on a very large scale. Thousands of customers must be serviced at a single POP and expensive networking equipment must be amortized over tens of thousands (maybe even millions) of subscribers.Network equipment manufacturers are consistently developing larger and more scalable equipment. Manufacturers are “leapfrogging” each other in a game of numbers – each claiming to support more subscribers on a single port or greater density within a single chassis. In fact, some vendors are now claiming to support more than 100,000 simultaneous PPPoE sessions or Subscribers on a single aggregation device.
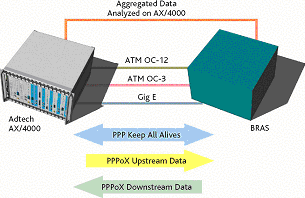
The diagram shows test for a typical network equipment manufacturer. In this example, the manufacturer wants to test approximately 100,000 concurrent PPPoA sessions on a single device, and run data and LCP Hellos (a.k.a. keep-alives) simultaneously on all of the sessions. Spirent’s AX/4000 PPPoX Emulation Suite allows the user to create 32000 sessions per port supporting ATM OC-3c, ATM OC-12c, Gigabit, and 10/100 Ethernet. This solution supports line rate data on each session with keep-alives and many other extensive features.
Understanding
how the Cisco Terminates PPPoE
- The Cisco initiates a Virtual Access interface (based on the Virtutal-Template configured) upon receipt of a PPPoE Discovery Initiaition (PADI). The Cisco will report (on the console) Interface Virtual-Access3, changed state to up
- Upon sucessful authentications, the Cisco will report (again on the console): Line protocol on Interface Virtual-Access3, changed state to up
- The Data Path
follows as shown in figure 7.
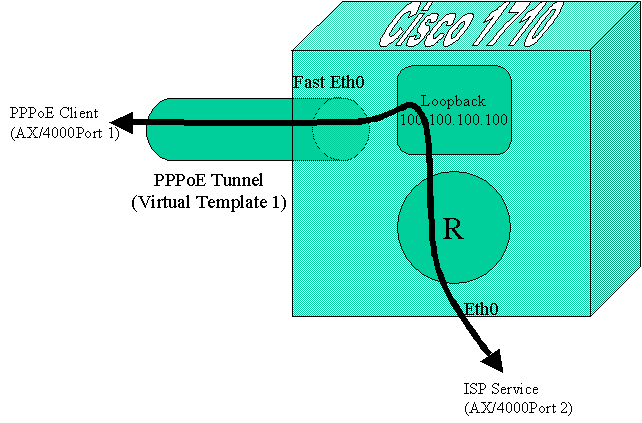
Fig. 7
References
- RFC 1055 A Nonstandard for Transmission of IP Datagrams over Serial Lines: SLIP
- RFC 1548 The Point to Point Protocol
- RFC 1661 The Point to Poin Protocol (superceds RFC 1548)
- RFC 2364 PPP Over AAL5, July 1998
- RFC 2516 A Method for Transmitting PPP Over Ethernet (PPPoE),
- February 1999
- PAP vs CHAP
Craig Miller January 2003