Back to Basics: NAT

|
by Craig Miller
NAT (Net Address Translation) is everywhere. Why unless you are using IPv6, you are probably going through two or more layers of NAT just to see this page.
It has become so common place that Network Designers/Architects, build it into the network without giving it a second thought. Need another router on your network, just let it do NAT. Even Google's supported Linux on ChromeOS uses two layers of NAT before the packet even hits the wireless interface.
Coming from an IPv6 point of view, NAT is a cancer, that rather than cutting it out, and taking chemo for six months, we say, "its OK, in fact, I'll add a couple more layers of NAT"
So let's take a closer look at how packets are forwarded, and what NAT is doing, and if there are any good uses for NAT.
IP Forwarding, plain and simple
You will remember from previous talks that a packet arrives at the router
- the ethernet header is discarded
- the route table is looked up, and an output interface chosen
- ARP/NDP will occur to get the destination MAC address of the next hop
- an ethernet header is prepended to the frame, and sent out
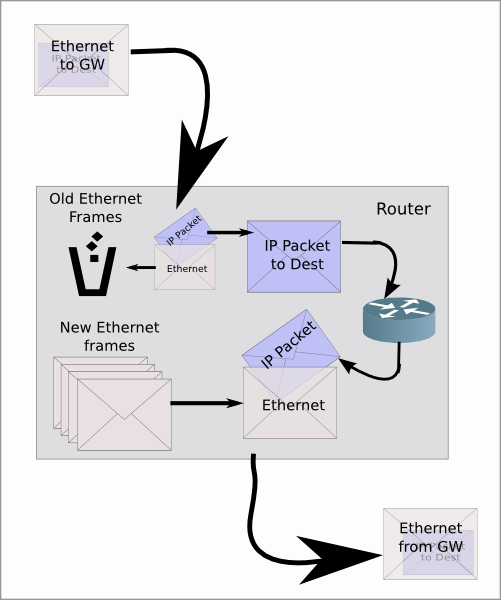
The router does this for each and every packet
In straight IP forwarding (for v4 and v6) there is no manipulation of the IP header. That doesn't mean that the router isn't doing any work when just forwarding packets. As it has been shown, ethernet headers are stripped and added, and in IPv4 the header checksum is validated.
The flavours of NAT
- NAT44 - is everywhere, breaks network connectivity, has extended the life of IPv4 by adding 16 bits to the 32 bits of IPv4. Can also change L4 port numbers, NATP
- NAT64 - Transition from IPv6 to IPv4
- NAT46 - Client part of 464XLAT, allows IPv4 to cross IPv6 networks, works in conjunction with NAT64
- NAT66 - Why would you need this? there is no shortage of address space
- NPTv6 - Network Prefix Translation
NAT44 v4 to v4
Why do we use NAT44? Originally specified in RFC 1631 in 1994 as a short-term solution to IPv4 address depletion.
This has become the most common form of NAT, as just about every home and business has an Internet connection which includes NAT (or NAT44 to differentiate it from other forms of NAT)
A look at a more complex home network with Router performing NAT44:
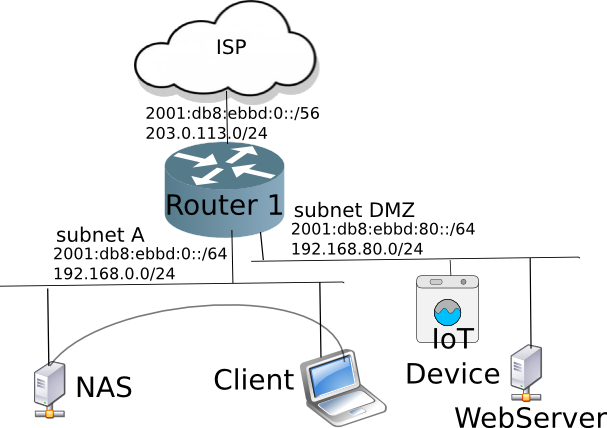
Looking at a packet as it traverses Router 1 from the LAN side (say, subnet A) to the Internet. Note how the IP source address, and sometimes the source TCP/UDP port is changed.
LAN
| Packet | Source | Destination |
|---|---|---|
| L3 | 192.168.0.10 | 192.0.3.1 |
| L4 | 5535 | 80 |
WAN after NAT44
| Packet | Source | Destination |
|---|---|---|
| L3 | 203.0.113.99 | 192.0.3.1 |
| L4 | 32749 | 80 |
NAT64 v6 to v4
NAT64 is used as a transition technology. It is meant to connect IPv6-only networks to the IPv4 Internet. It works in conjuction with DNS64, which creates synthetic AAAA records for hosts which don't have an IPv6 address. There is a well known prefix (WKP) which is used in NAT64 of 64:ff9b::/96, but it isn't a requirement that the WKP be used, any prefix in your address block can be used.
Note that unlike other IPv6 prefixes, this is a /96, rather than the usual /64. The reason for this is that NAT64 actually maps the entire IPv4 Internet into the last 32 bits of an IPv6 address (128 - 96 = 32).
Look at a similar example of a v4 destination of 192.0.3.1.
LAN before NAT64
| Packet | Source | Destination |
|---|---|---|
| L3 | 2001:db8:ebbd::10 | 64:ff96::c000:301 |
| L4 | 5535 | 80 |
WAN after NAT64
| Packet | Source | Destination |
|---|---|---|
| L3 | 203.0.113.99 | 192.0.3.1 |
| L4 | 5535 | 80 |
On the LAN side, the v4 address is converted to an IPv4 address of 64:ff96::c000:301 On the WAN side, the source IP is that of the router v4 203.0.113.99, and the destitation is the last 32 bits of the IPv6 destination address (hex c000:301 = decimal 192.0.3.1)
NAT46 v4 to v6
NAT46 appears to be similar to NAT64, but is actually used in partnership with NAT64.
Assume you have an IPv6-only network. You did this to keep things simple on your network, only one routing table, only one set of firewall rules, easier to troubleshoot and support, because you don't have to ask the customer which protocol they are using (and usually they won't know).
But you have some older equipment that doesn't support IPv6, or is too small, such as an ESP32 to support IPv6. How do those devices access the v4 Internet when they can't cross your IPv6-only network?
This is where NAT46 comes in. It will translate the packets from the legacy v4-only devices to IPv6. Those packets will cross the IPv6-only network, hit the NAT64 at the edge of your network, and translate them back to IPv4 to get onto the v4 Internet.
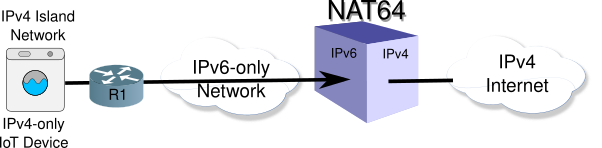
Router R1 is doing a NAT46 function. The header translation will look like:
LAN on v4 Island
| Packet | Source | Destination |
|---|---|---|
| L3 | 192.168.0.10 | 192.0.3.1 |
| L4 | 5535 | 80 |
WAN after NAT46
| Packet | Source | Destination |
|---|---|---|
| L3 | 2001:db8:ebbd::99 | 64:ff96::c000:301 |
| L4 | 5535 | 80 |
As you see, the headers on the LAN look like ordinary v4 headers. Router R1 translates the Destination Address to the WKP+hex(v4 dest) or 64:ff96::c000:301. Note that the Source address has also been changed, in this case, it is the WAN IPv6 address of Router R1.
NAT46 working with NAT64
Now roll back to NAT64, and you will see that the output (WAN side) of Router R1 is prepared to be an input to the NAT64 (using the WKP) where the packet is translated back to v4.
The combination of NAT46 and NAT64 is usually referred to as 464XLAT (RFC 6877). Will cover more of this technique in another presentation.
1. Hands On - Examining NAT at work: ping cra.ca
Download the following packaet captures, and open in Wireshark. The packet captures consist of 3 packets on the LAN, and after Network Translation 3 packets on the WAN.
NOTE: PCAP files are in two parts, the first set of packets are the input to the NAT device, and the second set of packets (in the same PCAP file) are the output of the NAT device
Discuss the following:
- In NAT44 which address is changed, Destination or Source?
- In NAT64 what is the IPv6 Destination Address?
- Why are both the source and destination addresses changed in NAT64?
- In NAT46 what are the IPv4 and IPv6 Destination addresses?
extra credit: How is the IPv4 address encoded in the IPv6 destination address of NAT64?
NPTv6 v6 to v6
Another type of NAT is Network Prefix Translation. The first 64 bits of the v6 address is known as the prefix.
The use case as stated in RFC 6296 is "provide address independence to the edge network". It allows an internal network to delay renumbering the network, should the ISP change their allocated prefix.
I am not a fan, if changing prefixes are a problem, there are two solutions: A) get another ISP, or B) apply for Provider Independent (PI) address space.
How does NPT work? It just swaps out the first 64 bits of the address with a different 64 bits. The last 64 bits (the Interface ID or IID) part remains unchanged. Therefore the headers look like:
LAN before NPTv6
| Packet | Source | Destination |
|---|---|---|
| L3 | 2001:db8:ebbd::10 | 2001:470:0:503::2 |
| L4 | 5535 | 80 |
WAN after NPTv6
| Packet | Source | Destination |
|---|---|---|
| L3 | 2607:f8b0:400a:809::10 | 2001:470:0:503::2 |
| L4 | 5535 | 80 |
The last 64 bits or 0:0:0:10 in the source address remain unchanged.
NAT66 v6 to v6 (again)
The last combination of NATs is NAT66, which works just like NAT44 but with IPv6. It is NOT an internet standard. There is no need for it, since NAT is an address conservation mechanism. As stated in RFC 1631, it is a method to conserve addresses.
With 340282366920938463463374607431768211456 or 3.4 X 1039 addresses, there is no need to conserve IPv6 addresses. There may be reasons to move to an IPv7, but it won't be because we ran out of IP addresses.
Therefore, there is no need for NAT66, and commercial equipment, like Cisco, don't support it. They support NPTv6 instead. Unfortunately, OpenWrt does not support NPTv6 directly, but there are nptv6 scripts which will do the job.
Getting from here to there
Sure, v4 and v6 are incompatible protocols. But there is a real need to translate from one to the other, and back again. Although NAT is evil and makes it harder to troubleshoot your network, there are some forms of NAT (such as NAT46 and NAT64) which provide connectivity to the legacy world.
* 2607:f8b0:400a:809 is a Google prefix
22 March 2021