NetSIG: Probing deeper with NMAP

|
by Craig Miller
Modern firewalls are stateful devices, attempting to make it appear that it is a transparent window to outbound traffic, but also look like a solid wall to (unsolicited) inbound packets.
Of course, the reason we run firewalls is to keep the bad guys out of our network. But did you know that a stateful firewall also automatically opens ports to allow traffic into your network?
This happens because when you send a request on your browser, for example, you are expecting a reply. The stateful firewall opens a port (usually TCP) to allow the response back into your network, and to your browser.
But there are other ways that ports can be opened on your firewall. The most obvious is manually. You set up a port forwarding rule to allow a specific port to a specific host on your network.
But it can also happen automatically, via a innocent-sounding protocol called Universal Plug and Play (UPnP). Originally created to allow games on your PC to open ports on your firewall, to permit the game to run.
But what if a bad-actor application, malware, were to start sending UPnP requests to your firewall? It could open your network to all sorts of bad things on the Internet.
If you are interested in security, I would recommend disabling UPnP on your router (it is not installed by default on OpenWrt).
Finding a Target
How do we go about looking for open ports on a firewall, or just a host (which can also be running a firewall)? There are scanners which can scan for hosts, usually by sending a ping, but there are more subtle methods as well, such as sending a TCP SYN packet, and listening for the TCP ACK return packet from the host (or target).
The first step in any network assessment is to discover which hosts or if you are on the internet, which targets are out there. As mentioned a network scanner is purpose-designed piece of software for this task.
But once you have a target, what then?
Using NMAP
Network Mapper (NMAP) can scan for Targets, but it really shines on looking deeper at a specific target and seeing what ports are open, using a variety of methods. And it can even determine what Operating System (OS) the target is running, which can provide even more insights into any weaknesses it may have.
When doing a network assessment, don't forget that closed ports on IPv4 do not equal closed ports on IPv6. Although both start with IP, they are not the same protocol, and it is very possible to have ports open on one and not the other. Fortunately NMAP supports both IPv4 and IPv6.
Looking for open ports
NMAP has a plethera of options. In fact, you can spend a lot of time looking at the options.
$ nmap -h
Nmap 7.70 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
...
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
...
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
In fact, the help goes on for 114 lines, with a total of 757 words.
Fortunately, there are some simple examples at the bottom of the help.

Simple run of NMAP
1. Hands On - Basic NMAP Open Port Detection
In this exercise, we'll be using the following network:
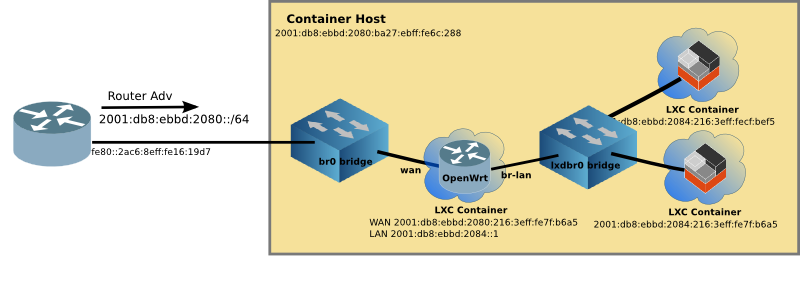
We'll be targetting one of the Linux Container servers on the right-hand side. Look for the target name on the Whiteboard
Use nmap -v -A <target> command to:
Attempt/Answer the following:
- Point NMAP at the target and record which ports are open?
- Run the same command using -6 parameter, are the same ports open?
- Which services are running on the open ports?
- What other info is reported on those services?
Discussion of NMAP Output #1
Analyzing the Target
nmap also has the ability to attempt to determine OS detection. Every OS networking stack has slightly different characteristics, for example the randomization of TCP initial sequence numbers. nmap uses this info to attempt a guess of the target OS.
One can use the OS info in a couple of ways:
- Good: consult information about the vulnerabilities on that OS, and upgrade the OS to prevent successful attacks.
- Bad: consult information about vulnerabilities on that OS, and attempt to exploit them
2. Hands On - Basic NMAP Open Port Detection
Use sudo nmap -O <target> command to:
Attempt/Answer the following:
- Point NMAP at the target and record the OS of the target
- Run the same command using -6 parameter, does NMAP report the same OS?
- Would you consider the OS reporting accurate?
- What does NMAP report when it can't determine the OS?
Discussion of NMAP Output #2
Reducing Threat Surface
As you can see, like Wireshark, nmap is a very powerful tool, which not only has straight port scanning abilities, but also offers excellent analysis capabilities as well.
By using nmap on our own hosts/devices, we can be aware of the services that are running, and disable un-needed one, and create firewall rules to restrict access to the other services as needed.
*NMAP screen Creative Commons
last updated: 24 January 2020