Openwrt and Netfilter

|
by Craig Miller
It has been a long time coming, but Netfilter have finally arrived in the latest release of OpenWrt (22.03.x). Netfilter brings network parity for IPv6, while improving firewall performance.
The Early Days
A little history, Linux has always had the concept of packet filtering, or a firewall. The original packet filter, ipfw, integrated into Linux in 1994, was based on a BSD ipfirewall. In Linux version 2.2 (1999), ipchains was introduced, but was stateless only. The Linux firewall evolved again with iptables in version 2.4 (2001), where stateful inspection returned.
iptables continued to evolve, but with separate streams, one for IPv4, another for IPv6, and yet another for the Ethernet (ebtables). Having multiple tables impacted performance, and led to kernel code duplication.
NFT
Netfilter's new packet-filtering utility, nft, replaces the older tools: iptables, ip6tables, arptables and ebtables.
At first look, nft options look quite a bit different from the old iptables.
nft --help
Usage: nft [ options ] [ cmds... ]
Options (general):
-h, --help Show this help
-v, --version Show version information
-V Show extended version information
Options (ruleset input handling):
-f, --file <filename> Read input from <filename>
-D, --define <name=value> Define variable, e.g. --define foo=1.2.3.4
-i, --interactive Read input from interactive CLI
-I, --includepath <directory> Add <directory> to the paths searched for include files. Default is: /etc
-c, --check Check commands validity without actually applying the changes.
-o, --optimize Optimize ruleset
Options (ruleset list formatting):
-a, --handle Output rule handle.
-s, --stateless Omit stateful information of ruleset.
-t, --terse Omit contents of sets.
-S, --service Translate ports to service names as described in /etc/services.
-N, --reversedns Translate IP addresses to names.
-u, --guid Print UID/GID as defined in /etc/passwd and /etc/group.
-n, --numeric Print fully numerical output.
-y, --numeric-priority Print chain priority numerically.
-p, --numeric-protocol Print layer 4 protocols numerically.
-T, --numeric-time Print time values numerically.
A key difference is that nft wants to read a json-like formatted file of rules, rather than just a simple (sometimes not so simple) command line of iptables.
The first useful command is to show the tables defined (on OpenWrt). Netfilter has a new address family, inet which applies to IPv4 and IPv6.
# nft list tables
table inet fw4
Unfortunately, for the new-comer, that doesn't appear to tell us much. But in fact, it is stating that there is a table of the family type of inet with the name fw4. A more informative command shows the chains and rules in the table (fw4):
# nft list table inet fw4
table inet fw4 {
chain input {
type filter hook input priority filter; policy accept;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname "br-lan" jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "wan" jump input_wan comment "!fw4: Handle wan IPv4/IPv6 input traffic"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname "br-lan" jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "wan" jump output_wan comment "!fw4: Handle wan IPv4/IPv6 output traffic"
}
...
chain forward_wan {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 4 bytes 416 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
meta nfproto ipv6 tcp dport { 22, 80, 443 } counter packets 1 bytes 80 jump accept_to_lan comment "!fw4: ext_mgmt_fwd"
meta nfproto ipv6 udp dport { 22, 80, 443 } counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: ext_mgmt_fwd"
jump reject_to_wan
}
...
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 ingress MTU fixing"
oifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone wan IPv4/IPv6 egress MTU fixing"
}
}
As you can see there are IPv4 and IPv6 rules in the Netfilter table. The nft man page is long but full of good info.
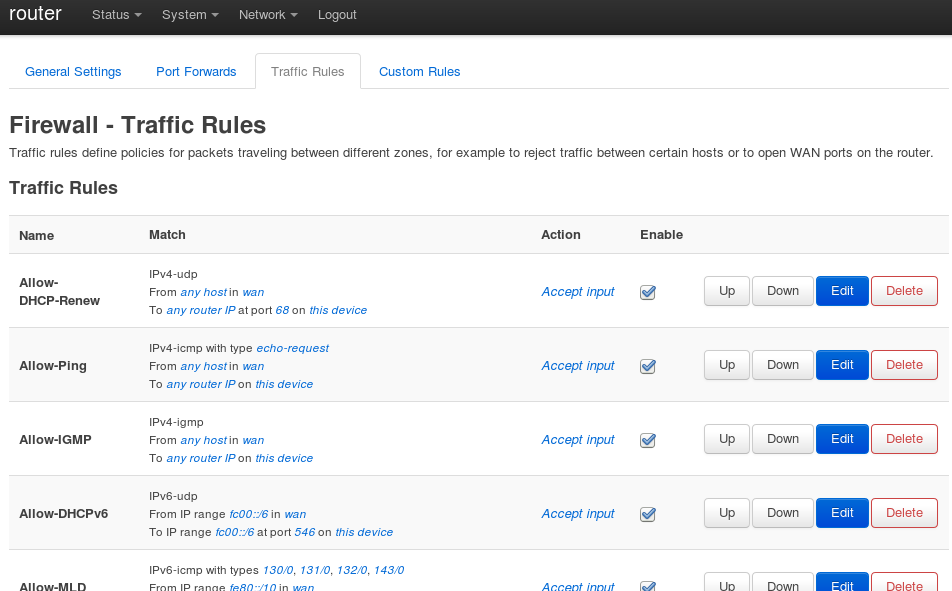
Firewall abstraction of OpenWrt
Fortunately, the developers of OpenWrt have kept the familiar web interface (LuCI) for firewall configuration, and the user doesn't have to know that nft is now managing everything, rather than the older tools: iptables, ip6tables, arptables and ebtables.
Conclusion
Why Netfilter? It reduces kernel code duplication, has more efficient execution, thus better performance, and adds atomic changes to filter rules.
Why OpenWrt? With the recent advent of malware targeting Small Office, Home Office [SOHO] routers, such as ZuoRAT, it is good to see an alternative to that old OEM router software, in a project which is active, and responding to security vulnerabilities.
nft has been around since 2014. Finally with the Netfilter address family of inet, IPv6 has equal status with IPv4. And with OpenWrt (22.03.x), your SOHO router will take advantage of a 21st Century firewall.
Photo Credit: NFT mania is here, and so are the scammers by Marco Verch under Creative Commons 2.0
16 July 2022