The future of the Internet - An IPv6 Fundamentals Tutorial
by Craig Miller
Outline
0. Introduction to Networking
- Internet addressing
- How packets are delivered?
- Why DNS is used?
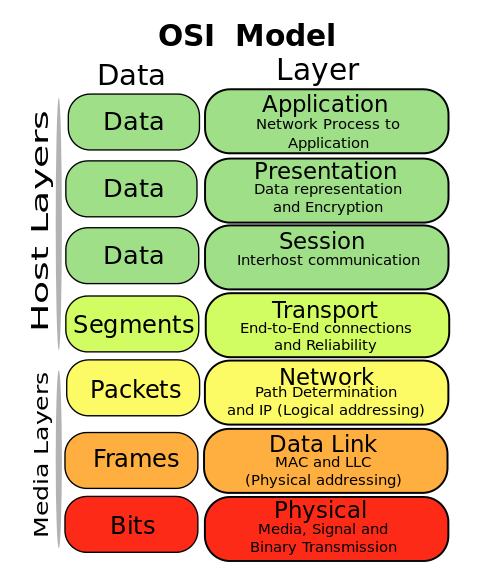
- Quick review of the OSI model
1. Why do we need IPv6?
The world has run out of IP addresses. IPv4 uses a 32 bit address which is a total of 4 billion addresses. However there are already 6 billion people in the world, and many of us have multiple devices, each with its own address. In order for the internet to continue to grow, a larger address space is required.
- Why not just add another octet to the address? like 10.192.168.0.1?
Adding another octet would require a new IP protocol, a change in the IP header, and all routers, computers, and devices connected to the internet. But only providing an additional 255 times the address space. This only delay the internet address problem for another 10 to 15 years, then we would require yet another overhaul of the entire internet.
For fun: a dramatization of running out of IP addresses.
Global Deployment of IPv6 is 18% of all internet traffic today as measured by Google
20% of traffic accesses Google over IPv6.
2. Not your Grandmother's IP
- IPv6 is a different networking protocol
- Standardized in 1998
- No interoperability between IPv4 and IPv6
- Don't assume it works like IPv4
- No ARP (Address Resolution Protocol), functionality replaced with ICMPv6 (Internet Control Message Protocol) Neighbour Discovery
- No Broadcast, uses Multicast
- Different network layer header

3. IPv6 Addressing
- How did we get here? As the size of networked devices increased, so did the need for address space

- IPv6 address is 128 bits long, think BIG
- It is that much bigger. 340282366920938463463374607431768211456 or 3.4 X 1039
- If the entire IPv4 address is equal to 1 meter (a little longer than a yard), then the entire address space of IPv6 is 18 trillion light-years.
- There are only 10^21 stars in the observable universe
- There are only 5.6x10^21 gains of sand on the earth
- No variable subnet masking, subnets are always /64
- Creates a sparely populated subnet, making it harder to scan for hosts (and attack)
- Scanning an IPv4 subnet, takes about 5 seconds, scanning an IPv6 prefix (aka subnet) takes about 7 days!
- End-user LANs are always /64, makes subnetting easy
- If you think a /64 is a waste of space, then you are still thinking IPv4-conserve-address-space
- RFC 7421 describes in detail why it is a bad idea to subnet larger than a /64
- Creates a sparely populated subnet, making it harder to scan for hosts (and attack)
- Multiple addresses are needed, at a minimum, a link-local (FE80::/10) and a Global Unique Address (GUA)
- Link-local address is auto-generated, and only unique per LAN segment, starts with FE80:
- Global Unique Address (GUA) will come from Router Advertisements (RA) via StateLess Auto Addressing Config (SLAAC)
- a Global address might look like:
2001:0db8:85a3:0000:0000:8a2e:0370:7334
- a Global address might look like:
When writing IPv6 addresses, it is common to use the compressed form, of substituting a double-colon :: for a single long string of zeros in the middle of the address. Thus 2001:0db8:0123:0000:0000:0000:0000:0010 becomes 2001:db8:123::10
Hands On - IP Addressing
Attempt/Answer the following:
- What IPv6 addresses are on your computer now?
- Can you tell the difference between a SLAAC and a DHCPv6 Address?
- Can you ping6 the router?
- What does the neighbour table look like? (hint, use the
ipcommand, or powershellGet-NetNeighbor) - Install Wireshark using
yum(for the next lab)
Look at Tools of the Trade
4. Router Advertisements
- The Network is in Control of addressing via Router Advertisements (RAs)
- Controls SLAAC (a-bit), and/or DHCPv6 (m-bit), or Other bit (o-bit)
- Auto Configuration Options
- RAs are periodically sent out by the router to all nodes (FF02::1)
- RAs are an ICMPv6 message type 134
- Sends Domain Name Server (DNS) information in the Recursive DNS Server (RDNSS) field
- Sends MTU size
- Sends the default gateway address (usually the link-local address of the router)
5. DNS is your friend
- Unless you have a very young brain, remembering hexadecimal addresses is going to be a challenge.
- DNS is an abstraction over the networking layer to make it easier for humans to remember addresses
- Quad A records (AAAA) are IPv6 address records
- AAAA records can be returned to the requester over IPv4 or IPv6
ping6by name rather than IPv6 address- DNS query/reply can be sent over IPv4 or IPv6. The reply, which may include IPv6 addresses can still be sent over IPv4
Intro to Wireshark
Hands On - RAs and DNS
Attempt/Answer the following:
- What Prefixes are being advertised by the router?
- Are the M, O, or A bits set?
- What is the IPv6 default gateway of your "PC"?
- Can you ping6 the router? Can you ping the router's link-local address?
- How many IPv6 addresses does google.com have?
- Use wireshark (or tcpdump) to see the DNS query/reply, what network protocol was used?
Sample Wireshark Captures
6. Firewalls - Naked without NAT, NOT!
Firewalls control the flow of traffic. They typically placed at choke points in the network, where control is more easily managed. Every modern home router has a stateful firewall, and the capability to do IPv4 NAT. Think of the firewall and NAT as separate operations which can both happen inside your router.
Make sure you set up the traffic rules on your IPv6 firewall before connecting to the internet. Do NOT block all ICMPv6 at the firewall, you will quickly become disconnected (ICMPv6 NDP and RAs are needed for connectivity).
-
Before there was NAT there were Firewalls
- Setup traffic rules which permit traffic to cross the firewall, and block all others
- Modern firewalls are stateful, meaning they can track traffic types (e.g. limit the rate of ping responses)
-
There is no NAT in IPv6, it isn't needed, since there are plenty of IPv6 addresses
-
IPv6 eliminates the evils of NAT
- Broken connectivity - The many to one nature of NAT breaks any to any connectivity originally conceived by the founders of the internet
- Simplifies Communications - Other traversal protocols like STUN (Session Traversal Utilities for NAT), TURN (Traversal Using Relays around NAT), IGDP (UPnP Internet Gateway Device Protocol), and ALGs (Application-level gateway) are no longer needed
- Easier Troubleshooting - Since the client address is the real address, and one doesn't have to look through one or more NAT devices to see the mapping of addresses just to troubleshoot a path
-
IPv6 supports address privacy extensions RFC 4941. These create a randomized IPv6 address (aka temporary address) every 24 hours to prevent tracking.
- to enable on Linux (as root)
sysctl net.ipv6.conf.all.use_tempaddr=2 sysctl net.ipv6.conf.default.use_tempaddr=2
7. Transitions
Since IPv6 is a different networking protocol, the network will be in a transition phase for sometime. The most common transitional method is Dual-Stack.
Transitional Mechanisms
-
Dual-Stack - The end station runs both IPv4 and IPv6, using the correct protocol when needed. However Dual-Stack requires double the configuration of all the network elements (routers, firewall, VPN, etc).
-
DNS64/NAT64 - Runs all connections over IPv6 using a special prefix (64:ff9b::/96) for IPv4 traffic. The special prefix traffic is then picked up by the ISP NAT64 device and translated to IPv4 on the internet. This method has the advantage of only maintaining one networking protocol in the network.
-
464XLAT RFC 6877 - is similar to DNS64/NAT64 but also supports IPv4-only applications such as Skype. T-Mobile has more than 10 million users using 464XLAT.
-
DS-lite - The home router issues IPv4 and IPv6 addresses as normal. But IPv4 traffic is encapsulated in IPv6 for transport (4in6) to the ISPs CGN (Carrier Grade NAT). IPv6 traffic travels natively through the ISPs network to the internet.
-
Tunnel Broker or 6in4 - Used to tunnel IPv6 traffic inside IPv4 to a Tunnel end point, where it is unencapsulated, and sent to the native IPv6 internet. Hurricane Electric is one of the largest providers of this service. Requires firewalls to pass Protocol 41 (6in4)
-
Teredo - Invented by Microsoft in 2003, standardized by RFC 4380. Encapsulates IPv6 in UDP over IPv4, therefore outbound UDP packets can not be filtered.
.gif)
Hands On -- Firewalls & Transitions
Attempt/Answer the following:
- What are some of the common problems with NAT?
- When using IPv6 NAT, what is the host source address?
- How to view ip6tables forwarding rules?
- Should the firewall block external all ICMPv6?
- Why not?
- How does ip6tables track traffic state?
- What is protocol 41?
- Use wireshark (or tcpdump) to see IPv6 header.
Look at Tools of the Trade
8. Operating System Support for IPv6
Most common OSs have had support for IPv6 since the mid 2000s. However the level of support has varied by platform. A more detailed comparison shows the subtle differences.
| OS | IPv6 Command |
|---|---|
| Linux (alpha 1996) (2.6 2005) | ip addr, ip neigh, ip route |
| BSD (4.x 2000) | ifconfig, sbp, netstat -r |
| BayRS (11.2 1999) | Used sitemanager to configure |
| Cisco IOS (2001) | show ipv6 |
| Windows (XP SP1 2002) | netsh show address, netsh show neighbors, netsh show route |
| Mac OSX (10.3 2003) | ifconfig, sbp, netstat -r |
| Android (1.0 2010) | No DHCPv6 support, v5.x+ uses RAs for DNS |
| Apple iOS (4.x 2010) | v4.3 DHCPv6 Support, v10.x IPv6-only support |
9. More on IPv6 Addresses and Scope
There are 5 types of IPv6 addresses:
- Unicast - 2000::/3
- Unique Local IPv6 Unicast - FC00::/7 (RFC 4193)
- Multicast - FF00::/8
- Link-Local - FE80::/10
- Loopback - ::1/128

At present the entire world of IPv6 addresses has been allocated out of the 2000::/3 range. To simplify global routing tables, the following prefixes have been allocated to geographical areas:
- 2001::/16 - historical
- 2400::/12 - Asia
- 2600::/12 - North America
- 2800::/12 - Latin America
- 2a00::/12 - Europe
- 2c00::/12 - Africa
The router will send an RA which will include a prefix (the first 64-bits of an address), which then each host will create a host unique last 64 bits, thus creating a globally unique unicast address.
Unique Local Address (ULA)
ULAs are used like RFC 1918 Private Addresses, in that they are not routed on the internet. But unlike IPv4, there are two key advantages over the familiar 192.168.0.0 address:
- No duplicate addresses. Addresses must select a random value for bits 8-48 (40 bits total)
- To help ensure that there are no duplicate addresses, there is a internet registry of addresses, while not required by the RFC is a good idea.
ULAs always start with FD.
Multicast Scope
The 4th byte of a multicast address represnts scope, or who wide will the multicast packet travel. For example, a multicast packet destine to all nodes on the link (will not cross a router) would be addressed to ff02::1 (all-nodes)
| n | Scope |
|---|---|
| 1 | Interface local |
| 2 | Link-local |
| 5 | Site-local |
| 8 | Organizational Local |
| E | Global |
Scope allows for more control of multicast than IPv4, which is always global, unless routers are not configured to forward it.
Link-Local addresses
Link-local addresses always start with FE80:: They are only significant on the link, and it is quite possible to have duplicate link-local addresses on different links. Link-local address is a basic unit of IPv6, since each host defines its own link-local address, the host does not need any other devices to create a unique address on the link. With that address, it can request services, such as requesting a RA from the router, and then DHCPv6 if the M-bit is set.
10. More on ICMPv6 and Neighbour Discovery

In order to send a packet whether close or far, and Ethernet header must be prepended to the datagram. In IPv4, in order to get the destination MAC address of the host or gateway router, an ARP (Address Resolution Protocol) is broadcast to all on the LAN. The host/router with that IP address responds with its MAC address.
Since there is no broadcast in IPv6, another method is required. Since each host has a link-local address at wake up time (boot), the sender can send out an ICMPv6 Type 135, Neighbour Solicitation, using the its link-local address as a source address. It will use use a multicast address, FF02::1 or FF02::1:ff41:44a (if the last three bytes of the destination IPv6 address are 41:044a).
The replying host/router will reply with a neighbour advertisement (type 136), a unicast packet with the Link-local destination address of the requester.
Hands On -- Addressing & Neighbour Discovery
Attempt/Answer the following:
- When would a ULA be used?
- What is the prefix assigned to your computer? What type of address is it?
- What type address does the host have for the default gateway
- What multicast addresses is your host listening to now?
- Use wireshark (or tcpdump) to see a neighbour discovery transaction.
11. IPv6 Header and Extension Headers
In order to quadruple the length of the IP address, but minimize the size of the IPv6 header, much of the information contained in an IPv4 header has been removed. The designers were able to squeeze in two (2) 128-bit addresses, in a 40 byte header.
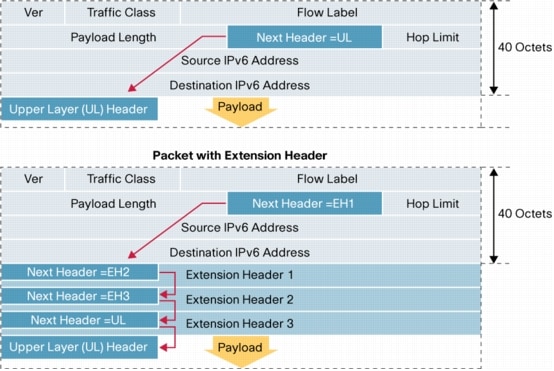
Extension headers are between the IPv6 header and the next header (typically TCP or UDP). The following types are defined by RFC 8200:
- Hop-by-Hop Options
- Routing (Type 0) - Removed by RFC 5095
- Fragment
- Destination Options
- Authentication (AH)
- Encapsulating Security Payload (ESP)
Extension Headers provide additional functionality when needed. More information can be found about extension headers from Loyola University.
Security implications of extension headers.
RA Guard has been devised to prevent the bad guys from sending out bogus RAs, thus attempting Man-in-the-middle attacks. Unfortunately, Cisco, created a hardware version of RA Guard, stepping 40 bytes into the packet looking for an ICMPv6 header with the Type 134 (RA). Unfortuntely, the bad guys quickly figured out if they put an extension header in between the IPv6 header and the ICMPv6 header (which is where it belongs), that they could defeat the hardware based RA Guard.
Therefore there IPv6 packets which come from the same LAN segment (think broadcast domain in IPv4) with the following extension headers should not be accepted: Hop-by-hop, Fragment, Destination options.
Hands On - Extension Headers
Attempt/Answer the following:
- Why are extension headers needed?
- How do AH and ESP headers differ?
- Use wireshark (or tcpdump) to look for IPv6 extension headers on the network. What extension headers are seen?
12. DHCPv6 & Prefix Delegation
DHCPv6 was standardized in 2003 by RFC 3315 and work similar to DHCPv4. However the options have different numbers, and a few additional options have been added, such as Prefix Delegation
-
DHCPv6 is controlled by the Network (via the RA) not by the client
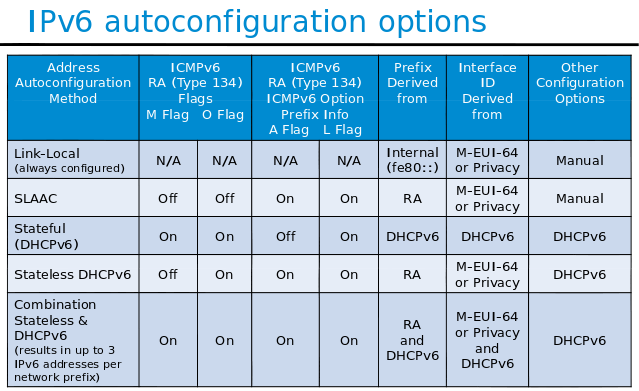
-
DHCPv6 uses a separate Client Identifier, called a DUID, DHCP Unique Identifier, which is more than a simple MAC address used by DHCPv4. The RFC allows three (3) types:
- Link-layer address plus time (most common)
- Vendor-assigned unique ID based on Enterprise Number
- Link-layer address
- Prefix Delegation, Option 25, is a mechanism by which an additional subnet/prefix is allocated to the requesting device to support a routable IPv6 network behind the device (avoids NAT). A sample pcap of DHCPv6-PD
Hands On - DHCPv6 & Prefix Delegation
Attempt/Answer the following:
- What is required before a client makes a DHCPv6 request?
- Why is Prefix Delegation needed?
- Does the host always get an IPv6 address from the DHCPv6 server?
- Use wireshark (or tcpdump) to look for the DUID Type in the Client ID option. What type is it?
- What are the other options in the client request?
13. Using IPv6 in the real world
- IPv6 in a URL - https://[2001:db8::1428:57ab]:443/
- IPv6 DNS - address lookup via AAAA records
- Google and IPv6
- IPv6 Backbone
- Security
- IPSec built into IPv6
- TLS (aka SSL) still works the same
- New security exploits are possible
- LAN services, RA+RDNSS or DHCPv6+DNS
- Google supports RA+RDNSS
- Microsoft supports DHCPv6+DNS
System V -> Systemd Network Configuration
The AT&T System V method of configuration has been around for decades, and is well understood. However in 2010, systemd was added to the Fedora Core repository by Lennart Poettering. The stated goal was to "Unify configuration" of the Linux systems. systemd has been adopted by the major Linux distros: RedHat, Ubuntu, Debian, Raspian.
There are a number of outstanding IPv6 bugs in systemd
Command to display systemd version: /usr/lib/systemd/systemd --version
LinOxide has a very good systemd cheatsheet

System V network configuration example
Network configuration is located in /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
#allow-hotplug eth0
#NetworkManager#iface eth0 inet dhcp
auto eth0
iface eth0 inet static
address 10.1.1.14
gateway 10.1.1.1
netmask 255.255.255.0
dns-nameservers 10.1.1.14 10.1.1.18
iface eth0 inet6 static
address 2001:470:ebbd:0::f014
netmask 64
Restart network services /etc/init.d/networking restart
systemd-networkd configuration example
Network configuration is located in /etc/system/network/<intf>.network
[Match]
Name=eth0
[Network]
DHCP=ipv4
Address=2001:470:ebbd:583::f014/64
IPv6PrivacyExtensions=yes
#IPv6Token=::12:34:56:78
Restart network services systemctl restart systemd-networkd.service
