Introduction to Networking
by Craig Miller
|
We all use computer networks, but like many other complex things in our life, we may not know how the nuts and bolts of how it actually works. In this talk, we'll cover the basics of networking including:
- Why do we need Ethernet anyway?
- The basics of IPv4 & IPv6
- What happens when a packet is routed
- Some basic SOHO network topologies
This talk does not cover:
- social networking
- interpersonal networking
- how to make friends and gain fame
History of IP
The Internet Protocol was developed in the 1970s as part of a DARPA (Defense Advanced Research Projects Agency) with the idea of creating a computer network which was self-healing.
IPv4 was developed as part of ARPANET (Advanced Research Projects Agency Network) in 1983 using a 32 bit address, at a time when four (4) billion addresses seemed like more than plenty.
In 10 years since IPv4 was standardized, it was apparent that the four billion addresses wasn't going to be enough, and work was started on the next Internet Protocol. IPv6 was standardized in 1998 and uses a 128 bit address or 340282366920938463463374607431768211456 or 3.4 X 1039 addresses.
But IPv6 is not just IPv4 with a larger address space, the IETF (Internet Engineering Task Force) also took the opportunity to fix some of the problems with IPv4 as well.
So why do we need Ethernet?
To understand why we need Ethernet and MAC (Media Access Control) addresses, one must first understand the OSI model. The model was developed in the late 1970s to provide a method of independence of networking functions.
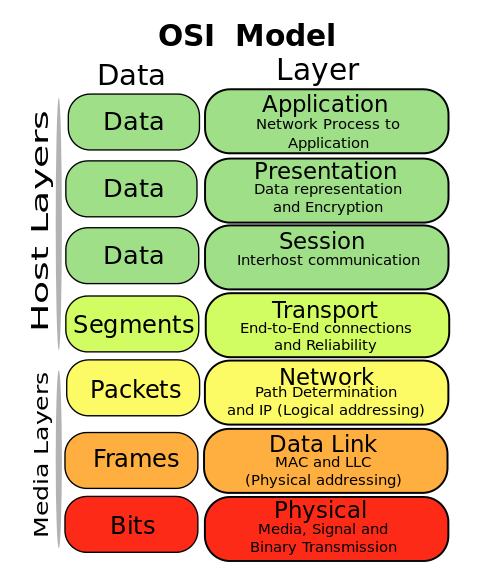
Ethernet was developed in the 1970s by Xerox PARC (Palo Alto Research Center). Originally it ran on coax cable as a method of transporting packetizing data. It fits in the Data-Link (L2) layer of the OSI Model.
There are other types of Data-Link technologies, such as DSL (Digital Subscriber Link) or DOCSIS (Data Over Cable Service Interface Specification).
Ethernet defines a 48 bit address and is standardized by the IEEE ( Institute of Electrical and Electronics Engineers) as 802.3. But as we'll see, Ethernet is only used to deliver your packet to the next node on the network, 48 bits is more than enough.
1. Hands On - Transporting a Packet
Pass the MAC envelope to another person, take the IP envelope out, and put it in another MAC envelope and pass to another person. At the IP destination, remove the data from the MAC envelope, and from the IP envelope
Discuss the following:
- Why all the encapsulation?
- Are MAC addresses globally unique?
- How does a router get the MAC address of the next Hop?
The Basics of IP
The Internet Protocol is a Layer 3 (network) protocol. But in the earlier days of networking there were many other networking protocols, such as Novell (IPX), AppleTalk, and NetBEUI (NetBIOS Extended User Interface used by Windows). Most of the other networking protocols were created by companies to allow their brand of computers to share info on a network, but were incompatible with other computer brands (think Apple not talking to Windows).
The Internet Protocol was independent of the companies promoting their own solutions, and it provided a path to much larger networks, eventually a world-wide network.
Both IPv4 and IPv6 ride on top of Ethernet. When looking at a wireshark capture, it is presented as IP is encapsulated in Ethernet. A handy Python networking tool, called Scapy represents the header layers with a slash "/". It is an easy way to represent the headers of the packets. For example, a basic web request might look like:
/Ethernet/IP4/TCP/HTTP/
/Ethernet/IP6/TCP/HTTP/
As you can see, because of the OSI model, it doesn't matter whether IPv4 or IPv6 is used as the network layer, when transporting HTTP requests.
The version 4 and 6 headers are different, as mentioned, not only was the address space increased to 128 bits, but other improvements were added as can be seen in the network headers:

Transport Layer
There are two common protocols that are used at the Transport Layer:
But there are many other Transport Protocols defined.
Port numbers
Both TCP and UDP have a 16 bit field (0-65535) for port numbers. The well known port numbers have been codified by IANA (Internet Address and Number Authority).
Common port numbers are 80 web, 443 secure web, and 22 ssh. Programs running on servers will listen to these ports depending on the service.
Application Layer
The IP stack tends it ignore Layers 5 and 6 of the OSI model, and the application protocol is typically found on top of the Transport protocol (layer 4).
As mentioned earlier, a webserver running on a server would listen to the web port 80 and the request and response packets would be in the form:
/Ethernet/IP4/TCP dst=80/HTTP/
/Ethernet/IP6/TCP dst=80/HTTP/
A SSH daemon would be listening to port 22 and the incoming packets would look like:
/Ethernet/IP4/TCP dst=22/HTTP/
/Ethernet/IP6/TCP dst=22/HTTP/
OSI model Summary
The key to understanding the OSI model, is to think where are packets decoded.
- Ethernet - by the network interface (think: eth0)
- IP - by the host/router, where do I send this packet?
- TCP|UDP - on the host, what application to I deliver the data to?
- HTTP|SSH - on the application, how to talk to the server application?
How do Routers forward packets?
Now that we have an idea of the different Layers of the OSI model, let's look at how Layers 2 & 3 work in more detail when traversing a router.
Let's use envelopes inside of envelopes to represent the different OSI layers, specifically Layers 2 & 3. When an Ethernet envelope arrives at your local router, the Destination MAC address on the the Ethernet envelope is the router itself, with an IP envelope inside. The router then does the following:
- Removes the Ethernet envelope and discards it
- Looks at the Destination IP address on the IP envelope and make a forwarding decision (e.g. which output port to use)
- Puts the IP envelope inside a new Ethernet envelope with the Destination of the next hop router/host
- Sends the new Ethernet envelope out the output port
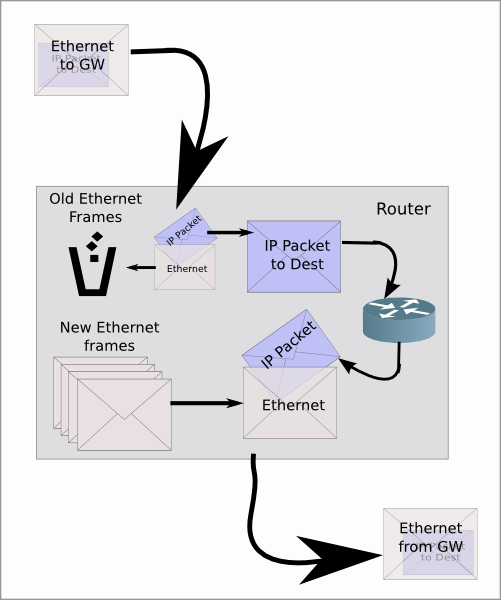
The IP envelope remains unchanged during routing (unless there is NAT, then it gets way more complex).
Sample SOHO Networks
Home Network
Having a DMZ network on a Home Network is recommended. In the future, there will be many IoT (Internet of Things) devices in your home. Placing them on their own network means that when they get hacked (security is usually an afterthought in IoT) your own IoT devices will not be able to attack your PC. Of course this means putting in router firewall rules to:
LAN -> DMZ = ALLOW
DMZ -> LAN = DENY
Simple Home Network
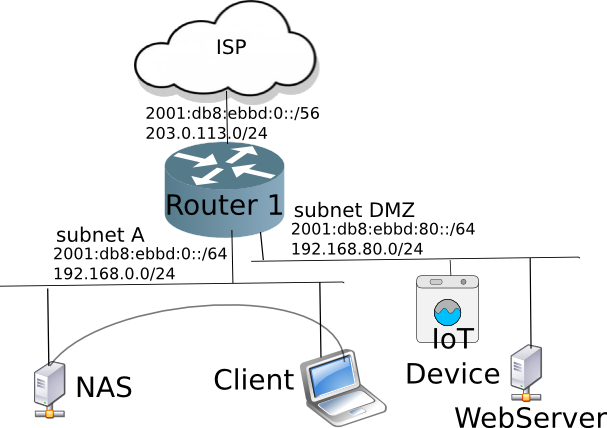
Small Office Network
In a small office network, again, it is a good idea to have a DMZ network.
But having multiple routers on your network means the routers must know about the other subnets on your network.
Using IPv4, the common way is on the router 2 to connect the WAN port to the upstream router 1. This has the cost of NAT, since router 2's default config is to NAT on the WAN port.
However, the NAT of Router 2 will prevent the Client (laptop) connecting to the office NAS. Of course you could put in a port-forward rule in router 2 to allow connections to the NAS on subnet B. But you would have to know details of the NAS protocol to map the correct ports, but it is starting to get overly complicated.
Another way in IPv4 is to disable NAT and run a routing protocol RIP (Routing Information Protocol). Some home routers support RIP (or even better RIP2), enterprise-network-providers (such as Cisco) certainly will. OpenWrt also supports RIP2.
In IPv6, multiple routers is automatic. Routers 2 & 3 will make a DHCPv6-PD requests to Router 1. Router 1 will Prefix-Delegate a subnet from the /56 block and automatically put routes in to its routes table pointing to Subnet B & C.
Of course you can run the IPv6 version of RIP, called RIPng, but in a hierarchical network, DHCPv6-PD works well enough.
Small Office Home Office Network
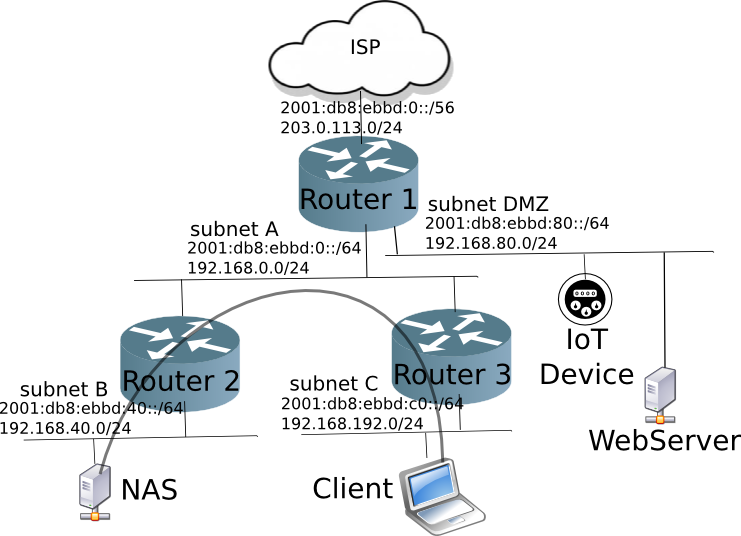
NAT in a SOHO network can cause network reachability issues (e.g. Client can't talk to the NAS server). When running multiple routers, it is important to run a routing protocol (RIP2 for IPv4 & RIPng for IPv6). Of course, if you are a router-head, then OSPFv2 (Open Shortest Path First) for IPv4, and OSPFv3 for IPv6 will have faster convergence times, but require more knowledge about routing protocols.
Using Traceroute(6)
Examining the router hop-by-hop path from here to there can be seen with the tool traceroute (and traceroute6).
(buster)cvmiller@localhost:~$ traceroute6 google.com
traceroute to google.com (2607:f8b0:400a:808::200e) from 2607:c000:8011:fd00:9916:a8d9:525e:b68c, port 33434, from port 44343, 30 hops max, 60 bytes packets
1 2607:c000:8011:fd00::1 (2607:c000:8011:fd00::1) 3.440 ms 3.546 ms 3.272 ms
2 2607:c000:8004::1 (2607:c000:8004::1) 40.701 ms 26.183 ms 24.900 ms
3 ae0-10-agg01-van2.teksavvy.com (2607:f2c0:ffff:4:4::151) 26.627 ms 26.894 ms 24.586 ms
4 v6-pr01-et-0-3-0-0.sea09.net.google.com (2001:504:16::3b41) 30.168 ms 27.902 ms 27.878 ms
5 2001:4860:0:1041::1 (2001:4860:0:1041::1) 39.874 ms 38.437 ms 39.881 ms
6 2001:4860:0:1::9bd (2001:4860:0:1::9bd) 27.977 ms 29.292 ms 28.964 ms
7 sea15s11-in-x0e.1e100.net (2607:f8b0:400a:808::200e) 41.566 ms 41.445 ms 41.291 ms
(buster)cvmiller@localhost:~$ traceroute6 -s 2001:470:ebbd:2084:82c5:f2ff:fe88:c8ed google.com
traceroute to google.com (2607:f8b0:400a:808::200e) from 2001:470:ebbd:2084:82c5:f2ff:fe88:c8ed, port 33434, from port 43924, 30 hops max, 60 bytes packets
1 2001:470:ebbd:2084::1 (2001:470:ebbd:2084::1) 5.669 ms 1.786 ms 1.905 ms
2 2001:470:ebbd:2080::1 (2001:470:ebbd:2080::1) 2.165 ms 3.018 ms 2.872 ms
3 2001:470:ebbd:2000::1 (2001:470:ebbd:2000::1) 3.432 ms 3.378 ms 2.746 ms
4 tunnel357924.tunnel.tserv14.sea1.ipv6.he.net (2001:470:a:b2c::1) 22.748 ms 22.889 ms 20.913 ms
5 10ge1-18.core1.sea1.he.net (2001:470:0:9b::1) 24.168 ms 21.891 ms 19.820 ms
6 v6-pr01-et-0-3-0-0.sea09.net.google.com (2001:504:16::3b41) 22.241 ms 19.919 ms 19.904 ms
7 2001:4860:0:1040::1 (2001:4860:0:1040::1) 20.895 ms 21.374 ms 20.167 ms
8 2001:4860:0:1::9bd (2001:4860:0:1::9bd) 20.082 ms 19.032 ms 19.766 ms
9 sea15s11-in-x0e.1e100.net (2607:f8b0:400a:808::200e) 19.532 ms 19.524 ms 19.234 ms
As you can see the route a packet takes depends on the source address. In the second traceroute, it can be seen the first three (3) router hops are on my own test network.
Need for sharing routing info
As I mentioned earlier there are choices in Routing Protocols, RIP2, RIPng, OSPF, but why are they needed?
When using multiple routers, it is important that they share information about the networks they are attached to with the other routers in the overall network. Take the following example:

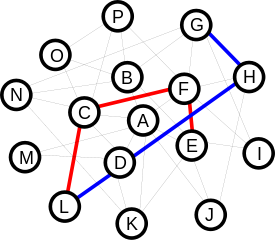
In the above network for A to get to D, there are two paths:
- A->C->D
- A->B->C->D
It may seem like path 1 is the natural choice to take, but in this example, there is a path cost between A & B of 23 (perhaps it is a slow dialup link). So taking the A->C link is expensive, so the shorter cost route is actually path 2.
Each node (A,B,C,D) advertise their directly connected links (e.g. Node A would advertise the A->B and A->C links) to the other nodes. Eventually these advertisements reach node D, and D now knows about links A->B and A->C even though it is not directly connected to either.
Self Healing
Should node B be turned off, the remaining routers will advertise that the links A->B and B->C are down, and traffic from A to D will be automatically re-routed to path 1.
Distance Vector Routing
This is called a Distance-Vector routing, RIP2 and RIPng are examples of DV Routing Protocols. The advantage of a DV routing protocol is they are pretty much turn on and forget. They may not be the most efficient, but they don't require a lot of routing knowledge to implement.
There are other non-DV routing protocols, such as OSPF and BGP, but they require more detail knowledge.
Getting from here to There in a SOHO Network

Back to the SOHO network, when running a Routing Protocol, Router 3 where the laptop is located, will know about Subnet B (connected to Router 2) via the routing protocol. When the Laptop wants to connect to the NAS, because the routers have shared routing info, a connection can be made.
The Internet
The advantage of the Internet Protocol (IP) is that has been able to scale to a world-wide sized network. The principles work the same, routing protocols exchange reachability information, and traffic can get from here to there.
4 April 2020