Summer Fun
by Craig Miller
Internet Radio
Can tune to any stream anywhere in the world. Like listening to shortwave, but clearer, don't have to wait until after sunset.
What's inside

Simple to use buttons along the top, with a 3 line character display.
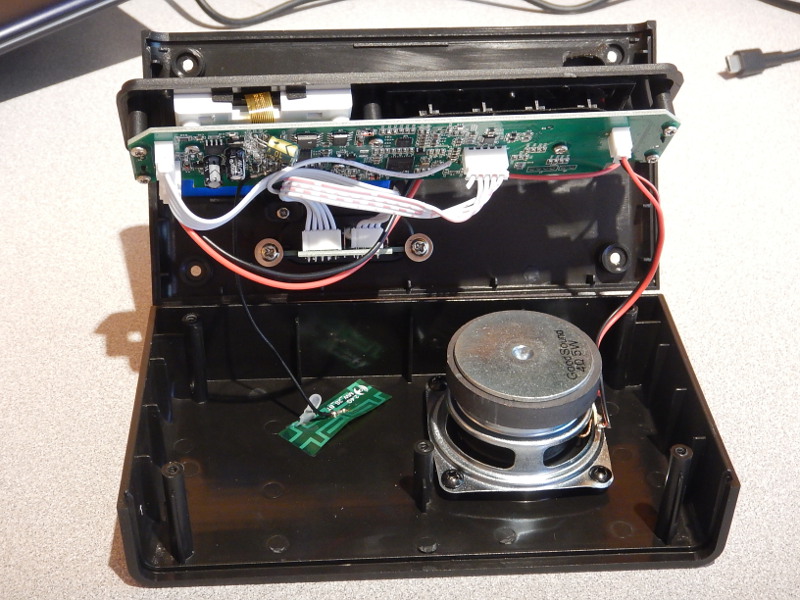
Simple construction inside. Single PCB board under the buttons, with wires to the 2.4 Ghz antenna, and speaker.

The brain inside, an ESP32, no wonder it doesn't support IPv6!
Internet Radio, just another IoT device
- Security of IoT is poor. Put all IoT devices, including Internet Radios, on DMZ network which protects the main network, should an IoT device get hacked
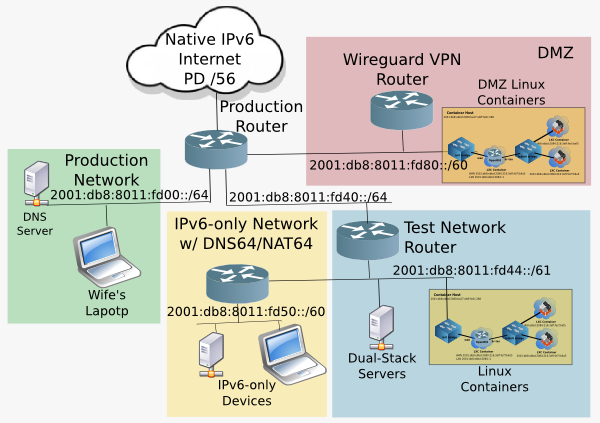
Production Router is also a multi-port firewall (running OpenWrt). IoT devices connect to the Wireguard VPN router via 2.4 Ghz Wifi.
The Internet radio:
- is IPv4-only
- Runs on an ESP32
- Has a nice local webserver for saving stations
- web page has IPv4 literal addresses embedded
Internet Radio has a built in Web Server
The documentation states that the laptop has to be on the same network as the Internet Radio. But my laptop is not on the DMZ network. So how to get there via IPv6?
- Solution
- Run a proxy
- socat, proxy at TCP layer, doesn't modify HTML on the fly
- nginx, will proxy and modify HTML on the fly
- Run a proxy
I used socat running on the router as a reverse proxy.
socat TCP6-LISTEN:8888,fork,reuseaddr,retry TCP4:192.168.99.36:80
Now to test it with curl
curl http://6nuuanu.hoomaha.net:8888/
<html xmlns='http://www.w3.org/1999/xhtml'>
<head><meta http-equiv='Content-Type' content='text/html; charset=UTF-8' >
<meta http-equiv='Pragma' content='no-cache'>
<meta http-equiv='cache-control' content='no-cache'>
<meta http-equiv='expires' content='-1'>
<meta http-equiv='set-cookie' content='Mon,12 May 2001 00:20:00 GMT'>
<script type="text/javascript">
<!--
window.history.forward();
function Click(){ return false; }
document.oncontextmenu = Click;
-->
</script>
<title>My Favourite</title><script type='text/javascript'>
<!--
document.oncontextmenu = function() { return false; }
-->
</script></head><noscript><font size="3" face="Arial"><font color="#FF0000"><b>This page requires javascript-enabled.</b></font></font><br>
<br>Please enable javacript and reload this page. Thank you.</noscript><frameset border='0' rows='94,*' cols='*' frameborder='no' framespacing='0'>
<frame id='frmHeader' src='http://192.168.99.36/top.cgi' scrolling='no' noresize><frameset border='0' rows='*' cols='24,*' frameborder='no' framespacing='0'>
<frame name='frmMiddle' id='frmMiddle' src='http://192.168.99.36/middle.cgi' frameborder='0' scrolling='no' hidefocus='true' noresize>
<frame name='frmContent' id='frmContent' src='http://192.168.99.36/content.cgi' frameborder='0' scrolling='auto' noresize hidefocus='true'></frameset><noframes>Sorry, your browser does not handle frames!</noframes></frameset></html>
However the HTML has IPv4 Literals in it.
Need to modify the HTML while proxying, enter nginx. Reverse Proxy is quite easy in nginx Create the foloowing config file:
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name localhost;
# Setup proxy
location / {
# sub module stuff
sub_filter_once off;
sub_filter 'http://192.168.99.36' 'http://6wr26.hoomaha.net';
# rev proxy config
proxy_pass http://wr26.hoomaha.net/;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
nginx reverse proxy config with on the fly HTML modification (sub_filter).
Now curl shows:
curl http://6wr26.hoomaha.net/
<html xmlns='http://www.w3.org/1999/xhtml'>
<head><meta http-equiv='Content-Type' content='text/html; charset=UTF-8' >
<meta http-equiv='Pragma' content='no-cache'>
<meta http-equiv='cache-control' content='no-cache'>
...
<frame name='frmContent' id='frmContent' src='http://6wr26.hoomaha.net/content.cgi' frameborder='0' scrolling='auto' noresize hidefocus='true'></frameset>
<noframes>Sorry, your browser does not handle frames!</noframes></frameset></html>
The real test, it works!
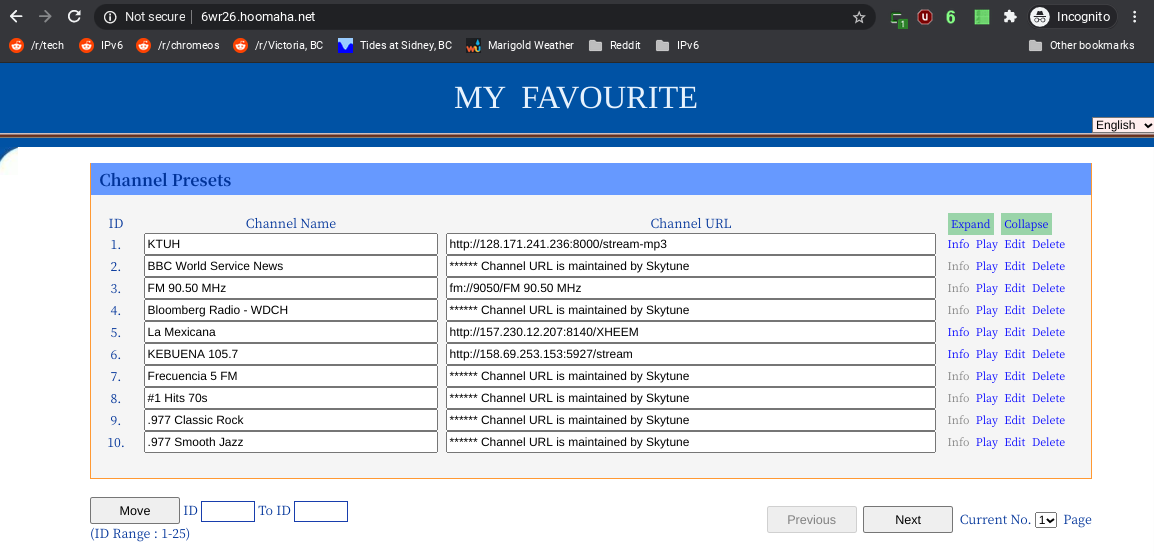
A Simple reverse Proxy works after all
By looking at the curl output a bit more, it is possible to make a request for just one frames contents in a browser. For example, put the following in into the browser http://6wr26.hoomaha.net/content.cgi
It will bring up just the important part of the page. Looking at the source, there are no IPv4 literals, so it is possible to use that URL with the simple socat proxy. Didn't need nginx after all.
http://6nuuanu.hoomaha.net:8888/content.cgi
More fun with Internet Radios
Peeking in on the web requests to see the real URL of the stream. By running tcpdump on the router where the traffic flows, it is possible to see the URL being requested.
tcpdump -i br-lan -A 'tcp[((tcp[12:1] & 0xf0) >> 2):4] = 0x47455420'
Options:
- -i interface
- -A output ASCII
- tcp filter Bit manipulation & shifting to search for string 'GET ' in TCP payload
The output looks like:
listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
14:43:27.086452 IP wr26.hoomaha.net.49972 > sc12.lax.llnw.net.80: Flags [P.], seq 471201:471333, ack 2322166818, win 15200, length 132: HTTP: GET /stream/bbcwssc_mp1_ws-einws HTTP/1.1
E...C.....V...c$E....4.P..0..it"P.;`....GET /stream/bbcwssc_mp1_ws-einws HTTP/1.1
Host: bbcwssc.ic.llnwd.net
User-Agent: WR-26/1.0
Icy-MetaData: 1
Content-Length: 0
Where you can see the real URL for the stream is: http://bbcwssc.ic.llnwd.net/stream/bbcwssc_mp1_ws-einws
Other Project:
- MotionEye
- Old bug from 2018 with fix
- decompyl6 to get source
- Modify source, remove pyc files
- Reboot, and IPv6 is going
12 September 2020