Upgrading the D-Link routers to OpenWrt

|
By Craig Miller
OpenWrt is my router software of choice. And with hundreds of supported home routers to choose from, it is usually easy to come by an inexpensive piece of hardware to upgrade to OpenWrt. Usually this is a simple affair, navigate to the firmware upgrade section in the OEM's software, and upgrade to the appropriate OpenWrt image.
Recently, while assisting a friend, I discovered that the old tried-and-true method no longer worked. D-Link had gone high-tech, and is now using signed images. What this means is that if the new firmware (or image) has not been cryptographically signed by the OEM, the router will reject the image. Naturally, OpenWrt, open source router software is not signed by D-Link.
Using the bootloader web interface to flash firmware
To D-Link's credit, they have put in a web-based firmware flasher in their bootloader. It isn't as nice as GL-iNETs web-based uboot flash utility, but it works with caveats.
- Start the router with the reset button depressed, it will be 192.168.0.1
- must manually assign an IP address to your laptop, such as 192.168.0.10
- the image must not be signed
The last one is the challenge, since D-Link only distributes signed images as of 2018.And, it rejects the OpenWrt image (some checksum error). So is there another way?
Hacking the D-Link router
Fortunately, I am not the only one who has wanted to install alternate router software on a D-Link router. Someone wrote a clever Python script (dir-882-telnet-hack.py ) to hack into the D-Link firmware. Using a vulnerability, a modified SOAP (Simple Object Access Protocol) command is sent to the router which starts a telnet server with no authentication.
Ack! D-Link has fixed this vulnerability
If you have a modern firmware on your D-Link router, then the telnet-hack python script won't work. Kudos to D-Link on fixing that security hole. Fortunately, they still have the older firmwares available, and it is just a matter of flashing an older signed image from D-Link.
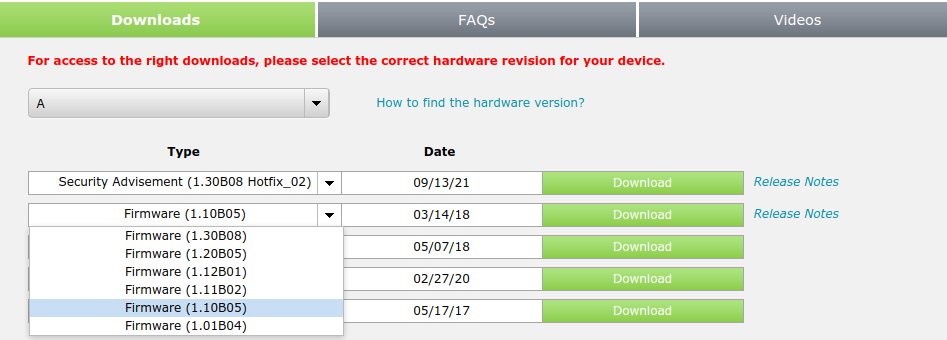
Just click on the down arrow, to find the older firmware. Version 1.10 is a good one to use, as it is signed and still has the telnet-hack vulnerability.
Flashing D-Link Firmware
Using the D-link Web GUI, navigate over to the firmware upgrade page (Management->Upgrade).
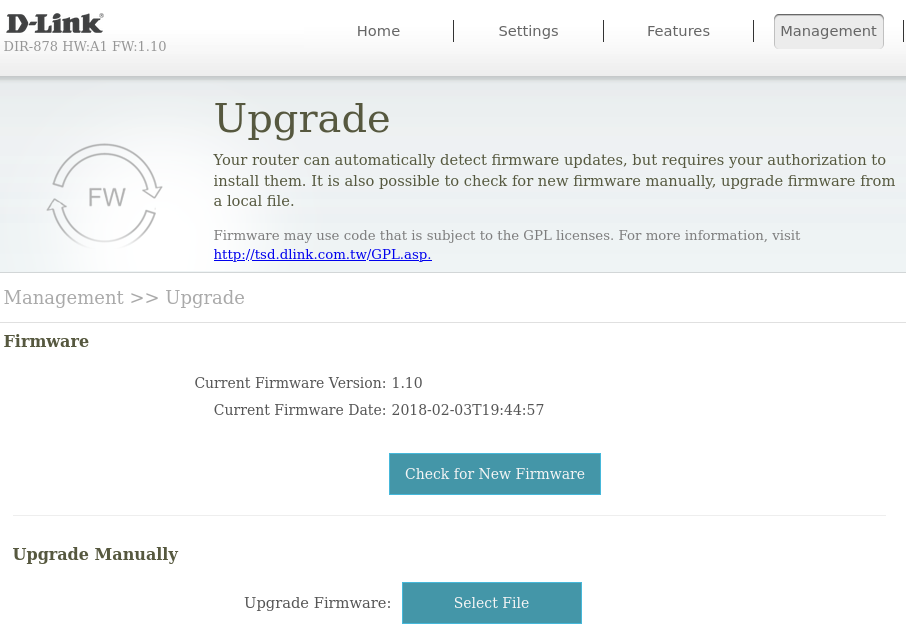
And click on "Select File" to open the older D-link firmware you just downloaded. Then upgrade (actually downgrading) the firmware. The router will reboot, and you will be running the older vulnerable firmware.
Back to Hacking
Once the router has been downgraded to a vulnerable version of D-link firmware, it is time to run the telnet-hack python script (dir-882-telnet-hack.py ).
- Connect your laptop via Ethernet to a router LAN port
- Observe that the laptop has an IP address (mine was 192.168.0.109)
- In a terminal window run the telnet-hack script, specifying the router IP address (most likely to be 192.168.0.1).
- Observe that the script reports "Exploit success"
$ python3 ./dir-882-telnet-hack.py 192.168.0.1
[*] Send payload to 192.168.0.1
[*] Exploit success!
[!] telnet 192.168.0.1
Then it is just a matter of telnetting to the router, and observing that you have logged in without a password challenge, and that you are root (the '#' prompt is usually reserved for root)
$ telnet 192.168.0.1
Trying 192.168.0.1...
Connected to 192.168.0.1.
Escape character is '^]'.
BusyBox v1.12.1 (2018-02-03 16:38:35 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
#
#
And you are in and have successfully hacked into the D-Link router. Leave that telnet session open for now, we'll come back to it.
Upgrading to OpenWrt
Use a browser to navigate to the OpenWrt Table of Hardware. Find your router, and click on the View/Edit Data link. This will take you to a more detailed info page about your router. It has good info, such as how much memory, storage, Ethernet ports, etc. Near the bottom, you will find links to the OpenWrt images.
For the D-Link DIR-878, it lists:
Firmware OpenWrt Install URL: https://downloads.openwrt.org/releases/21.02.1/targets/ramips/mt7621/openwrt-21.02.1-ramips-mt7621-dlink_dir-878-a1-squashfs-factory.bin
Download the Firmware OpenWrt Install image. The Key is that when flashing OpenWrt from OEM software, you want to use the factory image. And any upgrading afterward you should use the Upgrade image.
Loading the OpenWrt image onto the D-link router
In the D-Link Web GUI, navigate to the Upgrade page again (Management->Upgrade). This time click on "Select File" and select the OpenWrt image. The upgrade will fail, since the OpenWrt image is not signed. But that is OK.
Because what it did do is transfer the file to the router, and it is now in the /tmp directory on the router.
Back to our hacked telnet session
Switch back to your telnet session that we left open earlier. Change directory to the /tmp directory, and look for the image file. There is no MD5 sum to check. But if you are unsure, look at the size of the firmware file, and compare that to the OpenWrt factory image on your laptop. If they are the same, then got ahead and flash the image with mtd_write utility.
cd /tmp
ls -l firmware*
mtd_write -r -w write /tmp/firmware.img Kernel
The router will write the new image, and reboot. Congratulations, you have just upgraded your D-Link router to OpenWrt
When the D-Link reboots, OpenWrt IP will be 192.168.1.1
The Default IP address of OpenWrt is 192.168.1.1. You laptop should pick up an IP address on the 192.168.1.x network.
Point your browser at 192.168.1.1 and you should be presented a vanilla OpenWrt stating that there is NO PASSWORD. Just click log in and give it a password (System->Administration).
OpenWrt defaults with the Wireless interfaces disabled, so you must use Ethernet for the initial configuration. This is part of the security of OpenWrt. Go ahead and configure the Wireless (Network->Wireless), and don't forget to set a pass phrase under Wireless Security tab.
Welcome to Router freedom
OpenWrt is a open source Linux Distro with over 9000 software packages to choose from. You can configure your router to be a OpenVPN server, Wireguard VPN server, Adblocker (like PiHole), NAS server, even a DNS64/NAT64 translation device (for IPv6-only). Of course the router doesn't have enough storage for 9000 packages, but you have the freedom to modify your router they way you want. Not just what some OEM that you might want.
Go forth and enjoy OpenWrt and do what you want.
Additional Info:
- Upgrading D-Link routers with the telnet Hack (forum.openwrt.org)
- It is my understanding that the telnet-hack python script (dir-882-telnet-hack.py ) will work on most modern D-Link routers, once they have been downgraded to 1.10 D-Link firmware
- Caution: when flashing any firmware, ensure you have the correct image. In this article I am using an D-Link DIR-878, however if you have a DIR-882, be sure to use the D-Link firmware and OpenWrt firmware for that model.
- OpenWrt makes it easy to backup the configuration (System->Backup/Flash Firmware). Use it often, and it will make recovering from mistakes much easier.
- I found using an older version of Chrome (v84), would not log into the D-Link firmware, it always said the password was wrong. Using Firefox did not have this problem.
2 February 2022